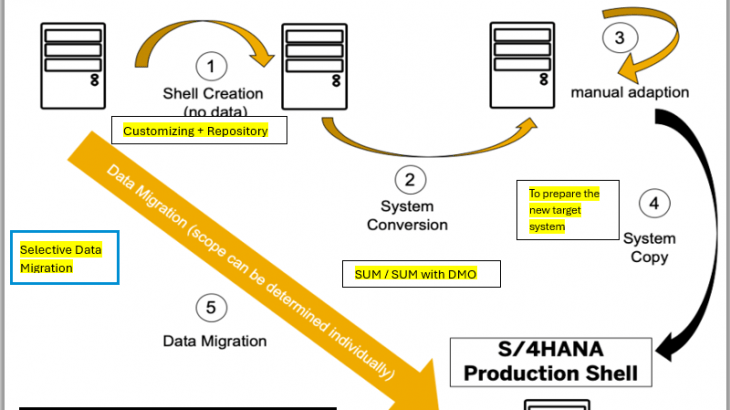
What is the Data Migration Cockpit? The Data Migration Cockpit is an SAP Fiori-based application designed to simplify and manage the migration of both master data and transactional data into SAP S/4HANA Public Cloud during system implementation. It provides a structured, user-friendly interface with the following key capabilities: With the Data Migration Cockpit, businesses can […]