Within SAP, we created a SAP Data Services Job to extract some recruiting data from SuccessFactors in order to store those data on an internal HANA system for reporting.
Since SAP Data Services 4.1, a specific adapter is available to connect with SuccessFactors. An adpater is a java service running in the background of Data Services which is able to deal with Cloud Web services. I would like to share with you some of my findings with SAP Data Services 4.2 and SFSF adapter.
Prerequisite
Please identify which Cloud instance of SuccessFactors you will use.

Please validate with this URL that you are able to open the connection from the SAP Data Services Job Server. To achieve this you need to ask SuccessFactors administrator the following things:
- provide an API user with proper authorization and password
- provide the Company ID
- Setup the data services IP address into the whitelist of SuccessFactors otherwise you will face this kind of error message

Adapter – Proxy Setup:
As your SAP Data Services is running in your internal network, please pay attention to the proxy definition by adding the following parameters in the adapter web interface setup:

Parameters to be added : -Dhttps.proxyHost=<proxy> -Dhttps.proxyPort=<8080>
Please also activate the Trace mode to True to have a view on trace and errors.
Certificate setup
If you receive this error below, you need to upload the right certificates in the keystore used by the adapter in order to enable the SSL connection (There are sometime mistakes in some documentations.)

Please perform the steps below:
Obtain 3 SFSF certificates
Below are the steps to export all certificates from the certificate path using FireFox.
1. Click on the lock
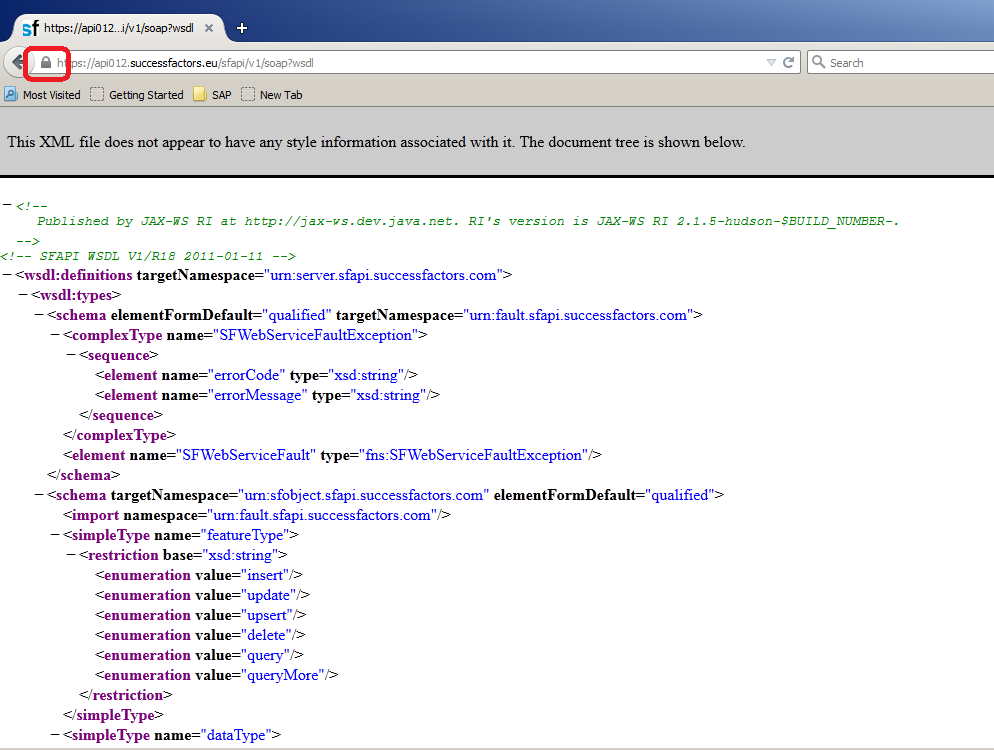
2. Click ‘More Information’
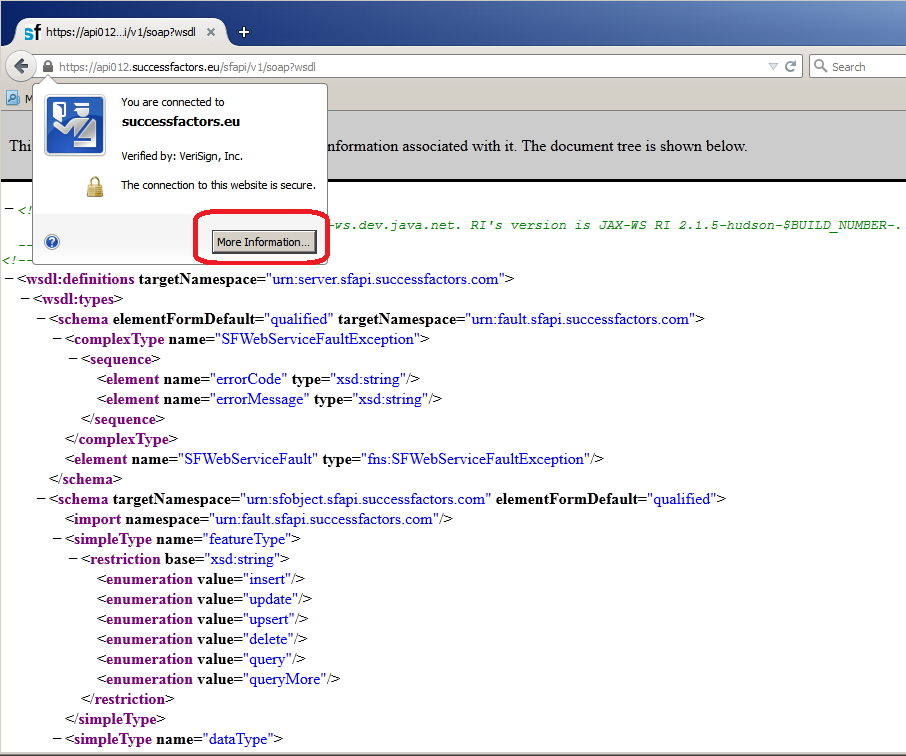
3. Click ‘View Certificate’
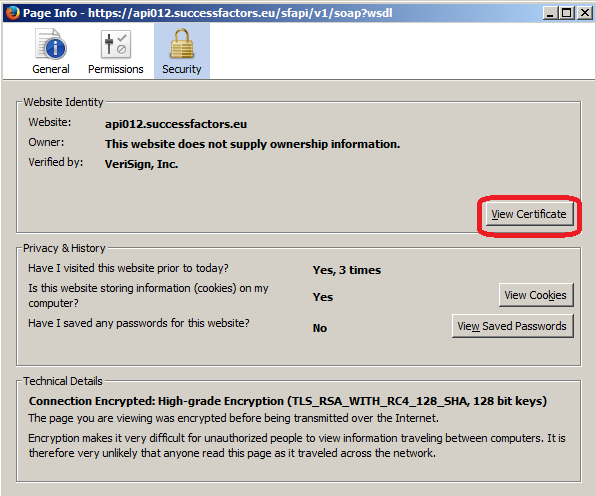
4. Click ‘Details’
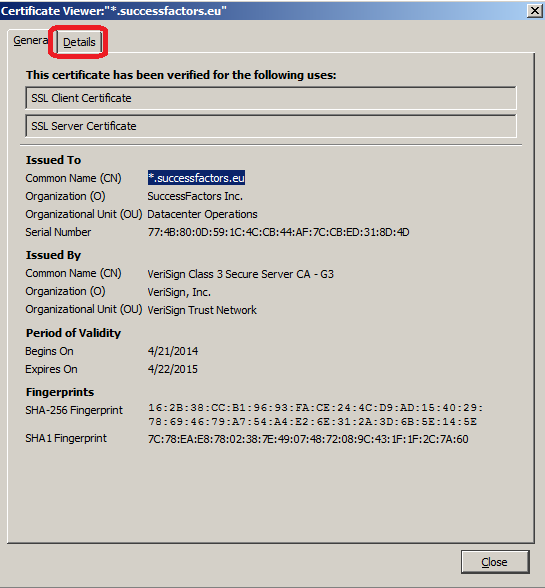
5. The ‘Certificate Hierarchy’ show 3 certificates – it is really important to get those 3 certificates to enable the SSL connection.
- The root certificate is ‘VeriSign Class 3 Public Primary Certification Authority – G5’.
- The child certificate is ‘VeriSign Class 3 Secure Server CA – G3’.
- The grandchild certificate is ‘*.successfactors.eu’.
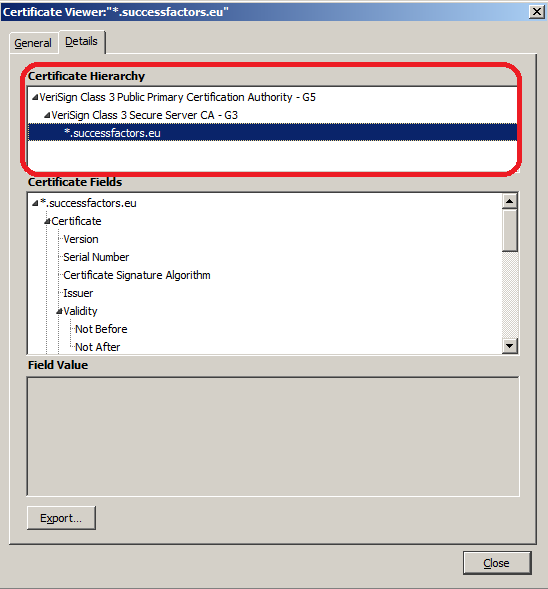
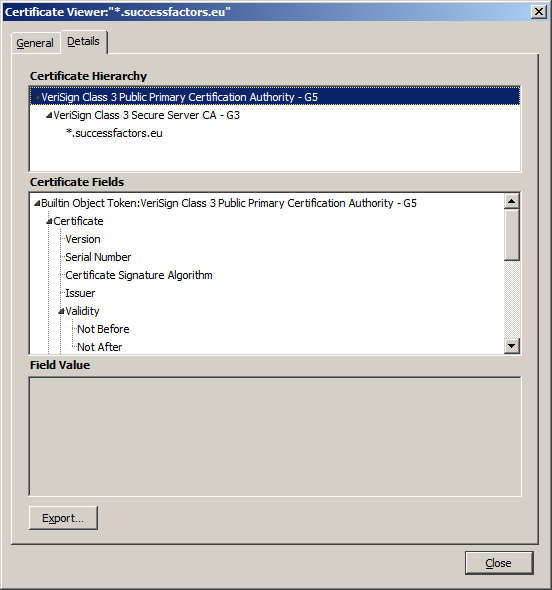
6. To export a certificate, click to highlight the certificate. Below shows how to export the root certificate.
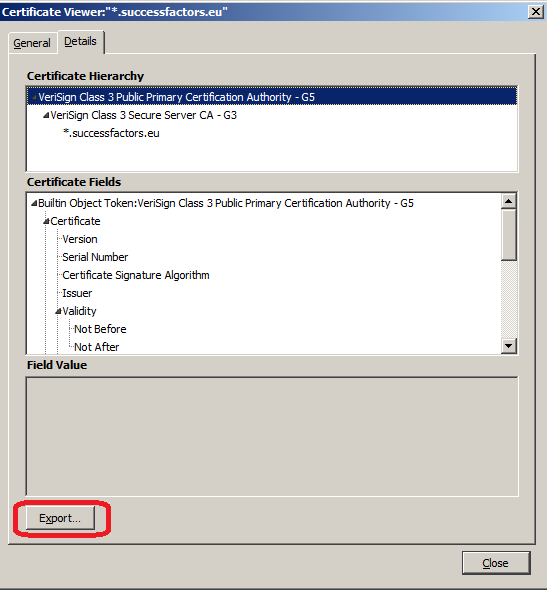
7. Click ‘Export’, to save the certificate file.
Upload those 3 certificates in the right keystore
a) Open a Dos command and Type set JAVA_HOME=%LINK_DIR%\ext and press Enter.
b) Type set path=%LINK_DIR%\ext\jre\bin;%path% and press Enter.
c) Type cd %link_dir%\ssl\trusted_certs and press Enter.
d) Type notepad sslks.key to view the keystore password.
e) Type keytool -import -alias verisign_class3g5ca -file “need full path to VeriSignClass3PublicPrimaryCertificationAuthority-G5.crt” -keystore jssecacerts and press Enter.
When ask ‘Enter keystore password:’, copy the password in step (d).
When ask ‘Trust this certificate? [no]:’, type yes
f) Type keytool -import -alias verisign_g3 -file “need full path to VeriSignClass3SecureServerCA-G3.crt” -keystore jssecacerts and press Enter.
When ask ‘Enter keystore password:’, copy the password in step (d).
When ask ‘Trust this certificate? [no]:’, type yes
g) Type keytool -import -alias sfsf_eu -file “need full path to sap.successfactors.eu.crt” -keystore jssecacerts and press Enter.
When ask ‘Enter keystore password:’, copy the password in step (d).
When ask ‘Trust this certificate? [no]:’, type yes
h) Restart the adapter
Nota Bene: In some technical documentation it is mentioned %LINK_DIR%\ext\jre\lib\security and to have the connection working properly we work here with \ssl\trusted_certs. In the technical documentation they mentioned the keystore cacerts and here we use jssecacerts.









