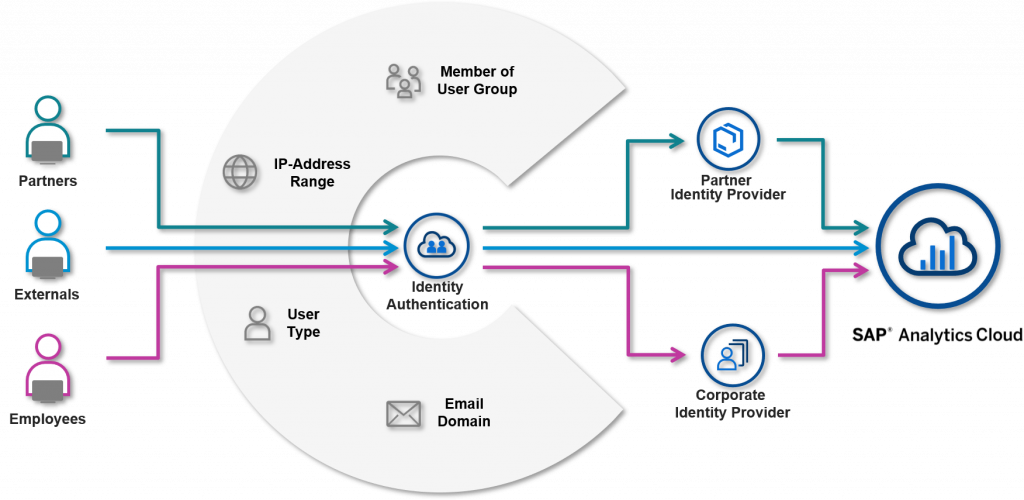
Currently, SAP Analytics Cloud supports a single SAML 2.0 Identity Provider (IdP). However, it is very common that identities from different user groups or various regions need to be authenticated by different Identity Providers, and customers still want to continue using their existing authentication processes and IdP(s). For example, the identities of your employees are managed in the Corporate IdP; your partners are managed in the Partner IdP; and your customers are managed in External IdP. Now you want to share the usage of one SAP Analytics Cloud tenant among all the users. In this case, it would be great that SAP Analytics Cloud could support multiple Identity Providers for user logon.
How can you achieve the user logon for SAP Analytics Cloud that is authenticated by different Identity Providers? This blog demonstrates a solution that you can configure a central Identity Provider functioning as a proxy to delegate authentication to Corporate IdP. An IdP proxy enables you to create structures of trust relationships that ultimately simplify the management of your Identity Providers. SAP Analytics Cloud only needs to trust the IdP proxy, no matter how complex the authentication process is behind the IdP proxy. This solution makes it possible to setup multiple Identity Providers for SAP Analytics Cloud.
A proxy relationship involves the following parties:
- Identity Provider Proxy
An Identity Provider can function as a proxy for another Identity Provider. It is a central SSO endpoint that connects applications with Corporate IdP(s). SAP Cloud Identity Service – Identity Authentication service (IAS) is able to provide full support as IdP proxy. - Corporate Identity Provider
The Identity Provider stores and manages digital identities of employees and users in your corporation, and companies use it to allow employees and users to connect with applications. - Service Provider
A Service Provider (SP) hosts a service that users want to access. This Service Provider trusts the IdP proxy. In this scenario, SAP Analytics Cloud is used as the Service Provider.
There is no direct trust relationship between the corporate Identity Provider and SAP Analytics Cloud that the user is trying to access. SAP Analytics Cloud only needs to trust the IdP proxy, and SAP Analytics Cloud doesn’t care how many corporate Identity Providers are connected with Identity Provider proxy, or how complex the authentication rules are defined behind Identity Provider proxy.
Landscape Setup
Let me lead you through a customer’s scenario. In the customer’s landscape, there is a Corporate IdP managing the identities for internal employees, and External IdP for external users. To allow both internal and external users to log onto SAP Analytics Cloud, an IdP proxy is needed in front of the customer’s IdPs and SAML SSO is configured between the IdP proxy and SAP Analytics Cloud.
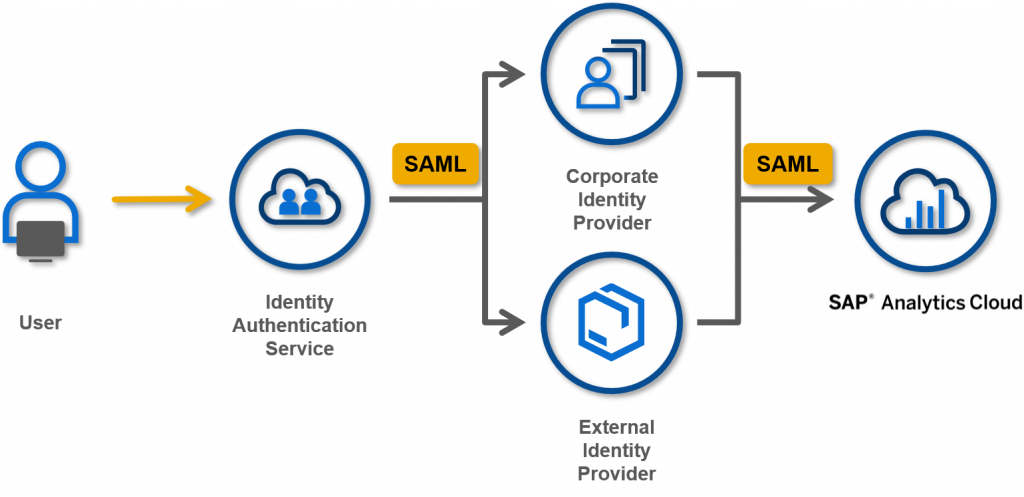
Note: In this blog, both Corporate IdP and External IdP are IAS tenants. But they could be any SAML-complaint Identity Providers, such as Microsoft Active Directory, Ping Identity, Okta, etc.
Additionally, the customer also needs to make the following SAML-based features work in SAP Analytics Cloud:
- Dynamic user creation
New users can be automatically created using the default role and will be able to use SAML SSO to log onto SAP Analytics Cloud. - Automatic team assignment based on SAML attributes
Users can be automatically assigned to teams based on their SAML attributes. - User logon using Conditional Authentication
Employees can be authenticated via a Corporate IdP based on the email domain and user group, and external users can be authenticated via External IdP based on the IP address. - Direct Live Data Connection with SAML SSO
Users have a single sign-on experience to live connect to the data sources.
In the next steps, I will show you how to setup such a landscape, and also meet the customer’s requirements.
Configuring Identity Authentication Service as the Proxy to Corporate Identity Provider
Before running through the configuring steps, let’s download the SAML 2.0 metadata from all three IdPs.
1. Configure Trust on the Corporate Identity Provider
Access the Corporate IdP’s administration console and create an application for the central IAS as a proxy. As shown in the following screenshot, the application is named as ‘IAS proxy’.
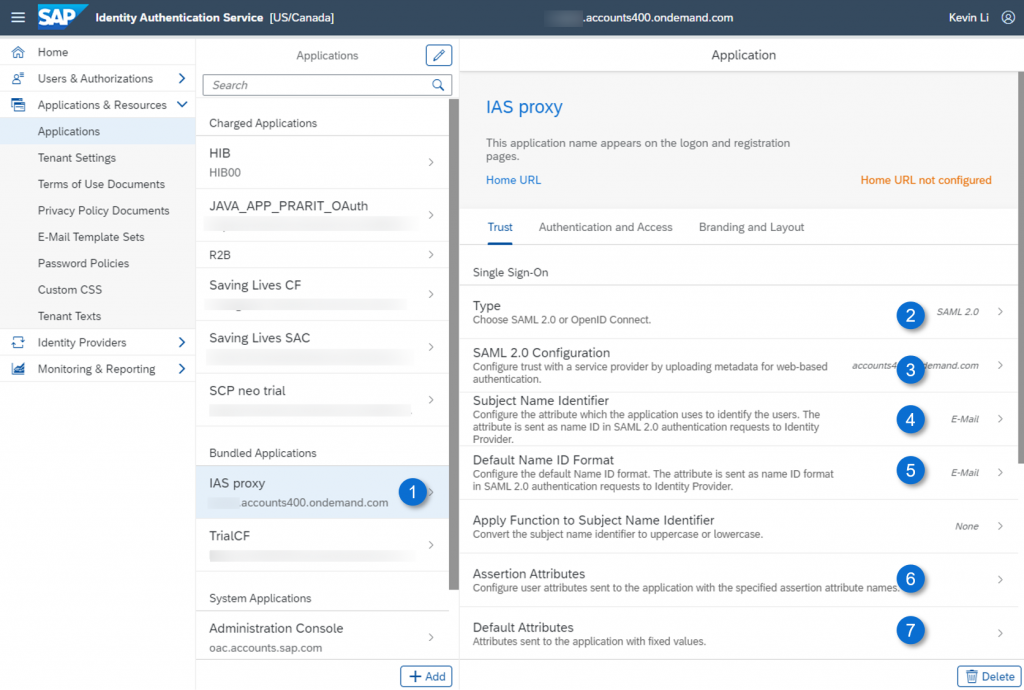
Under Trust, set the below values:
- Type – SAML 2.0
- SAML 2.0 Configuration – Upload the metadata from IdP proxy tenant
- Subject Name Identifier – Set it as ‘E-Mail’
- Default Name Identifier – Set it as ‘E-Mail’
- Default Attributes – Add attribute ‘Groups’, and its value ‘sac’
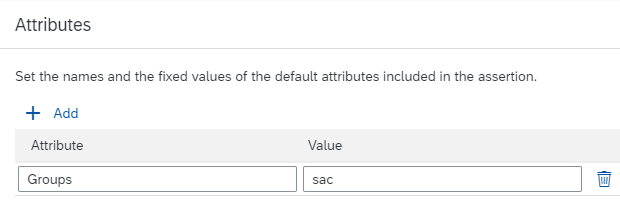
Since the customer wants to automatically create the users and assign the users to different teams in SAP Analytics Cloud, we have to add the Assertion Attributes in SAML configuration. These SAML attributes will be used as user profile and team mapping attributes.
- Assertion Attributes – Add a new SAML assertion attributes for group ‘sac’ as shown below. These SAML attributes will be used later for dynamic user creation, team assignment, role mappings between Corporate IdP and SAP Analytics Cloud. SAP Analytics Cloud has a list of case-sensitive assertion attributes.
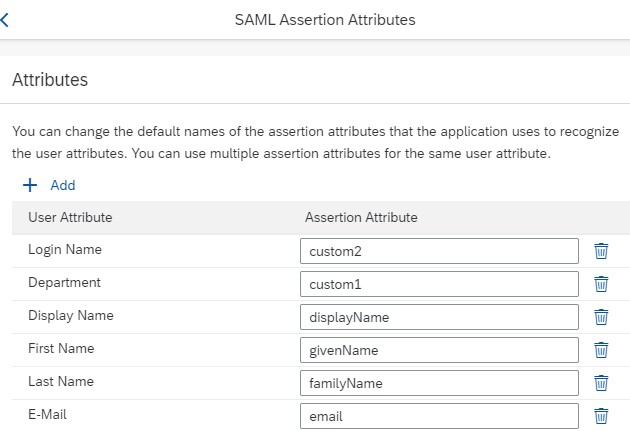
Tenant administrators can configure whether the attributes are taken from the assertion of the corporate identity provider or from the user store of Identity Authentication. With that said, the above SAML attributes can also be added from IdP proxy tenant, if the users have profiles in IdP proxy tenant. The Identity Federation option allows you to choose whether the user attributes are taken from the corporate IdP assertion or from Identity Authentication user store. You can also restrict access based on the user profile, and additionally apply the custom application configurations for the authentication and access policies.
2. Configure Trust on IdP Proxy
Switch to IdP proxy’s Administration console. In the “Corporate Identity Providers” menu, add a new corporate IdP and provide a name like “Your Corporate IdP”.
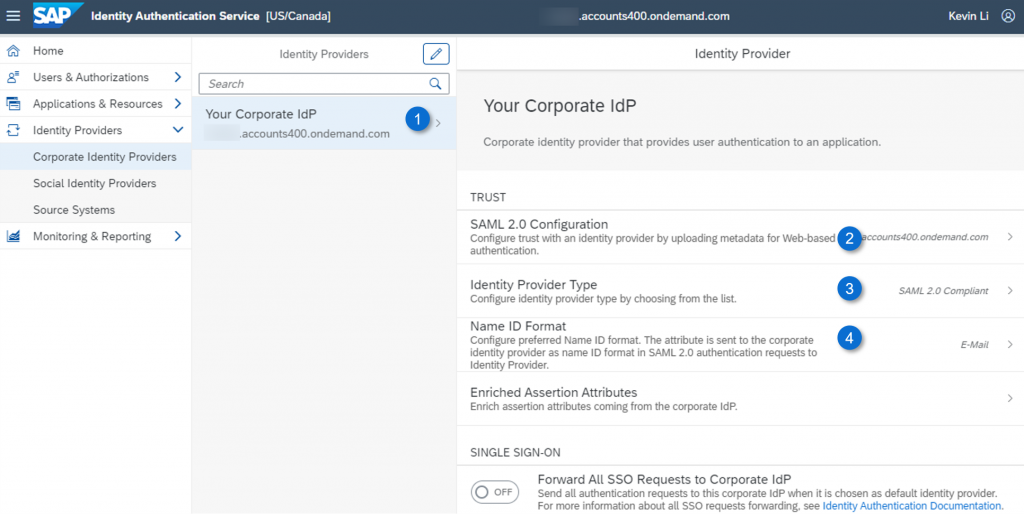
- SAML 2.0 Configuration – Upload the metadata from your corporate IdP
- Identity Provider Type – Set it to “SAML 2.0 Compliant”. Set this value accordingly if your corporate IdP is Microsoft ADFS/Azure AD or SAP Single Sign-On.
- Name ID Format – Set it as ‘E-Mail’
Save the configurations and we have completed the setup of the IdP proxy to Corporate IdP. Similarly, we need to repeat the same configuration for the External IdP. Once the configuration is done for the External IdP, you can move onto the next steps.
User logon using Conditional Authentication
To ensure that different users can logon SAP Analytics Cloud via different Identity providers, we need to use Conditional Authentication in IAS. IAS tenant administrator can control the access to an application by defining different rules for the authenticating identity provider. Based on these rules, users are authenticated either via a corporate identity provider or via Identity Authentication.
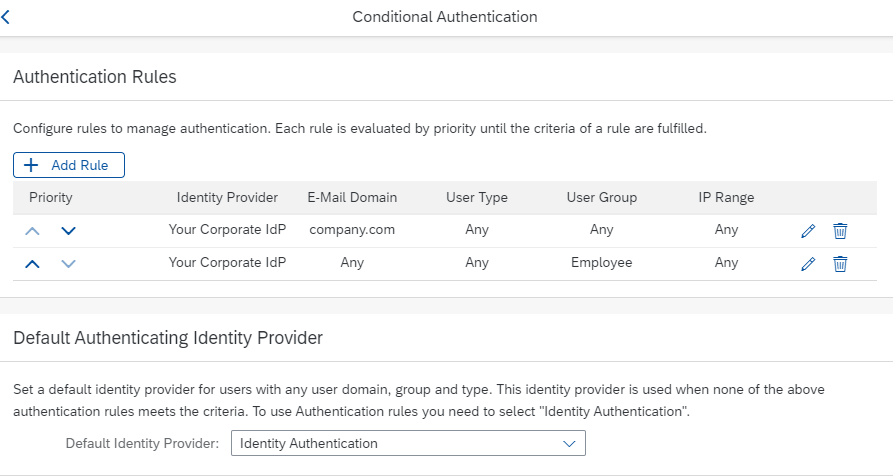
Click on the application ‘SAP Analytics Cloud’ in Identity Authentication proxy, and open Conditional Authentication. We can define rules for authenticating identity provider according to e-mail domain, user type, user group, and IP range. As shown in above image, users who use your company E-Mail, or belong to user group ‘Employee’ will be authenticated via corporate IdP. Next, you need to define rules for your external users based on IP addresses, so that the external users will be authenticated via External IdP.
Configuring Identity Authentication with SAP Analytics Cloud
Once you complete the above configurations, we can navigate to SAP Analytics Cloud Administration and configure the trust between SAP Analytics Cloud and IdP proxy.
1. Enabling a Custom SAML Identity Provider in SAP Analytics Cloud
For detailed step-by-step instruction, please see SAP Help. I am pointing out two steps here:
Step 2: Upload the metadata from IdP proxy tenant
Step 3: Select ‘Email’ as the user attribute type and enable Dynamic User Creation
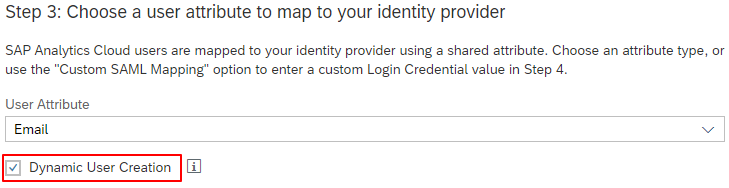
Once Dynamic User Creation is enabled, new user profile will be automatically created using the SAML attributes for First Name, Last Name, Display Name, etc.
2. Configure SAP Analytics Cloud as Service Provider in IdP Proxy
Navigate back to the IdP proxy’s Administration console and create an application under Applications and Resources menu.
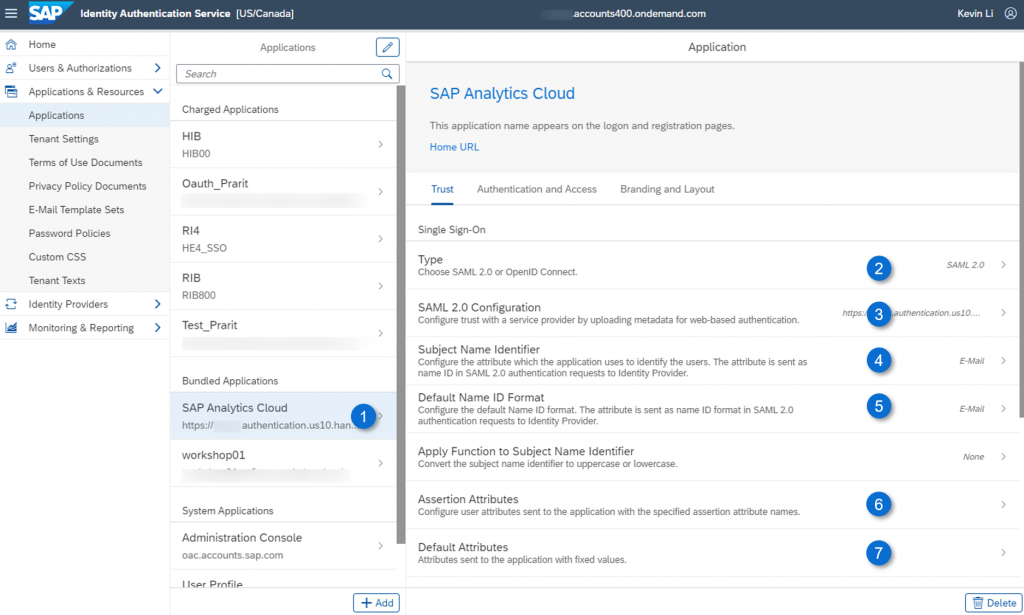
Under Trust, set the below values:
- Type – SAML 2.0
- SAML 2.0 Configuration – Upload the metadata from SAP Analytics Cloud tenant
- Subject Name Identifier – Set it as ‘E-Mail’
- Default Name Identifier – Set it as ‘E-Mail’
- Default Attributes (optional) – Add attribute ‘Groups’, and its value ‘sac’
- Assertion Attributes (optional) – Add a new SAML assertion attributes for dynamic user creation, team assignment, role mappings between Corporate IdP and SAP Analytics Cloud
The Default Attributes and Assertion Attributes are not required, if you already configured them at corporate IdP level. In case that the needed assertion attributes exist only in IdP proxy, which means the user profiles also exist in IdP proxy, you can then add the assertion attributes here. All you need to do is to switch on the Identity Federation under the corporate IdP as shown in the following screenshot.
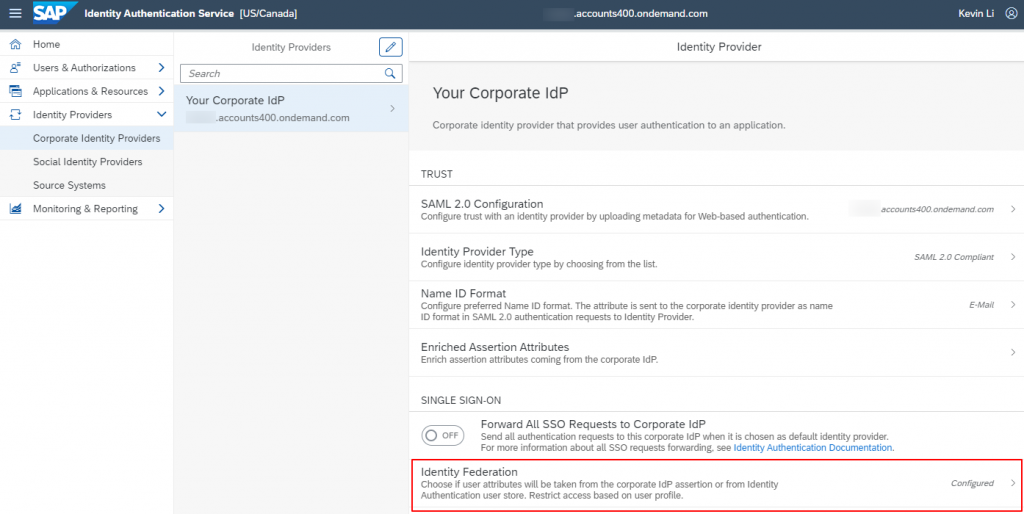
Assigning Users to Teams Using SAML Attributes
In SAP Analytics Cloud, the SAML assertion attributes can be also used to assign users to teams or assign roles to users. Since the 2 features use the same SAML mechanism, I choose ‘Assigning users to teams’ as an example to show you the configuration.
Go to Teams menu, click on create SAML Team Mapping.
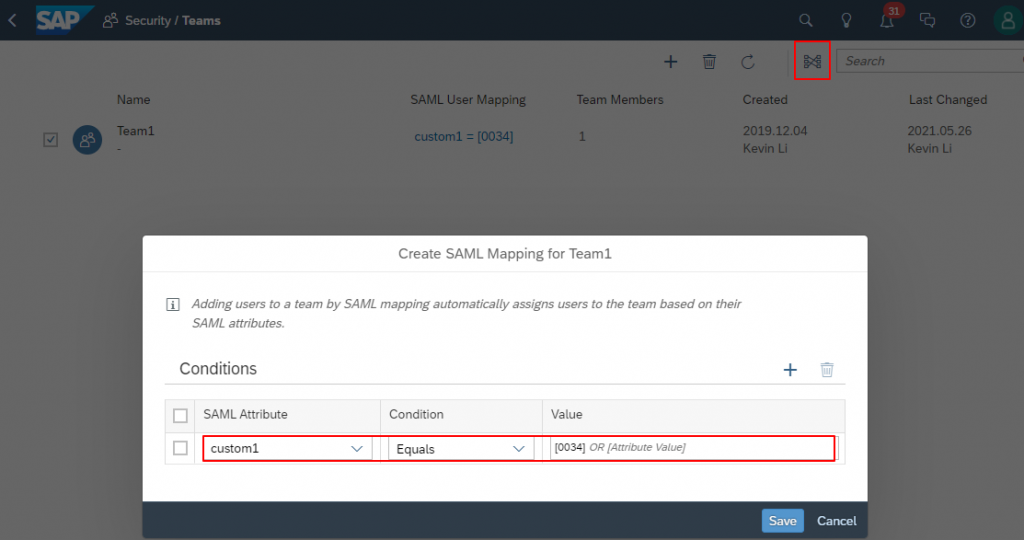
In the pop-up window, I add a new condition. In the previous section, I configured assertion attribute ‘custom1’ mapping to the user attribute ‘Department’, and the value of ‘Department’ in corporate IdP equals to ‘0034’. (In case you don’t know the value of a user attribute, the value can be found in SAML response.) Thus, I added ‘custom1’ equals ‘0034’ as the SAML attribute to assign users to Team1.
Live Data Connection with SAML SSO
Let’s move on to the last customer’s requirement: setup Live Data Connection with SAML SSO. Specifically, the customer wants to live connect to SAP HANA with SAML SSO, and to allow only employees have access to SAP HANA. To enable Live Connection to SAP HANA with SSO, we need to configure the InA package (/sap/bc/ina/service/v2) for SAML authentication.
In this scenario, we have 2 options to configure SAP HANA with SAML SSO:
- using IdP proxy to Corporate IdP
- directly using Corporate IdP
Next, I will explain the 2 options and share the best practices for you to choose the better option for your landscape.
1. Using IdP Proxy to Corporate IdP
Similar to what we have configured for SAP Analytics Cloud, you can still make use of IdP proxy which is already configured with your Corporate IdP. The only configuration is to establish the trust between SAP HANA and IdP proxy and define the rule for employees to be authenticated via Corporate IdP.
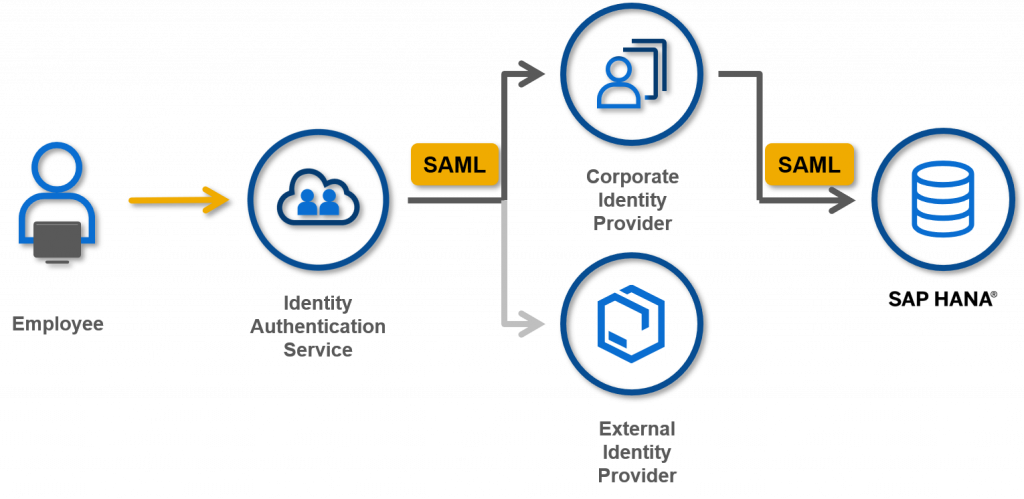
The advantages of this option are to make use of the central IdP proxy to simplify the management of different Identity Providers, and it can be easily expanded to External IdP in case that the external users need access to SAP HANA in the future.
2. Directly using Corporate IdP
You can also configure SAP HANA as a Service Provider directly in your corporate IdP. In this case, the employee will not go through IdP proxy, and the trust relationship will be established between SAP HANA and Corporate IdP.
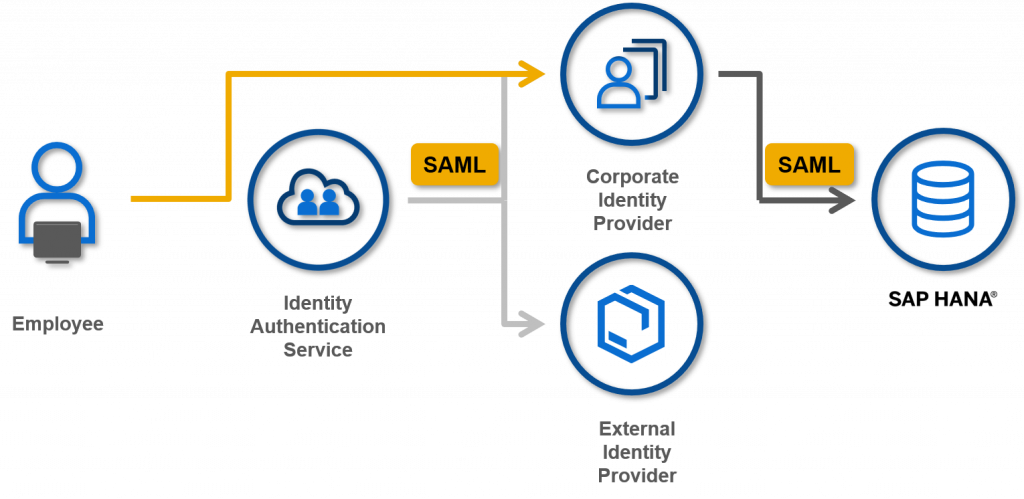
The advantages of this option are that you don’t need to configure Conditional Authentication for SAP HANA, and the performance of the authentication process becomes a bit faster. Moreover, you don’t have to use ‘Email’ as Subject Name Identifier in SAP HANA even if ‘Email’ is used between IdP proxy and Corporate IdP. You can configure any other user attributes like User ID, Employee Number as the Subject Name Identifier in SAP HANA.