SAP Identity Management (IDM) is a key component of the security portfolio of SAP, which is responsible for managing the identity master data of employees, externals, administrator, and other entities.
SAP IDM is one central location for managing the user Identities and permission (privileges and Business role), synchronizing data between system and application and maintaining password across connected systems i.e. both SAP and non-SAP systems. Hence, with use of SAP Identity management tool, companies can manage and provide user access in different heterogenous environment securely and efficiently.
Now one needs to make sure that the SAP IDM is Compliant across SAP Landscapes in one integrated solution. This can be achieved by Integrating SAP IDM with SAP Access control where one can do risk validation before provisioning.
Using this solution, SAP IDM can execute provisioning to multiple target systems (ARQ) which are controlled by SAP Access Control to ensure compliance according to the rules implemented here in Access control (ARA).

When Integrating SAP Identity management with SAP Access Control, one first needs to understand how the identity data is exported and imported between SAP IDM and SAP access control.
So, let’s start with discussing the components of SAP Identity Management that are used in the following way:
1. VIRTUAL DIRECTORY SERVER
- It accepts the requests from Identity Center.
- Deals with all connection to/from SAP Access Control through the web service API exposed by SAP Access Control.
Optionally, another Virtual Directory Server can be deployed as an Identity Service on an AS Java server that deals with event-based result handling.
2. IDENTITY CENTER
- Contains the workflow tasks and the necessary jobs that drive the risk validation using SAP Access Control, before provisioning based on the
- Provisioning Framework for SAP Systems.
Communicates with the Virtual Directory Server (VDS) using the LDAP protocol.
Depending on the communication defined between Identity management and Access Control, one can trigger below calls for implementing role synchronization.
- RFC Communication – This is used when implementing Business role synchronization. (GRC 12.0) where the Identity Center – Runs Initial Load Business Roles job by making an RFC call to GRC
- Web Service Communication – This is used when implementing scenarios for technical roles (privileges).
INTEGRATION SCENARIOS
The integration scenarios exist based on two factors:
- Landscape Configuration
- Result Handling
Now the GRC Provisioning Framework can be configured accordingly to deal with any combination of these two.
LANDSCAPE CONFIGURATION SCENARIOS
There are two landscape configuration scenarios for the integration:
CENTRALIZED PROVISIONING
The centralized provisioning is recommended as a default solution. This is a scenario where SAP NetWeaver Identity Management is the only provisioning system, responsible for provisioning both the assignments requiring and not requiring compliance checks to the systems (both SAP and non-SAP). The SAP NetWeaver Identity Management uses SAP Access Control to execute risk analysis.


DISTRIBUTED PROVISIONING
This Solution is recommended to use in exceptional cases only. In this scenario, the provisioning is performed both by SAP Identity Management (IDM) and SAP Access Control. SAP IDM is responsible for provisioning assignments not requiring compliance checks to multiple target system (SAP and Non -SAP), while SAP Access Control is used for provisioning assignments requiring Compliance checks to SAP ABAP target system.

RESULT HANDLING SCENARIOS:
Whenever SAP Identity Management sends a request to SAP Access Control, further action depends on the results of SAP Access Control’s request processing, i.e. which privileges are approved, and which are not.
Two different approaches to handling a request processing result exist and only one of them can be active at a time.
- Polling: The Identity Management performs the appropriate web service request, polling the SAP Access Control for the result. This result handling scenario is fail-safe.
- Event Based (AC Call-back services): Instead of polling for the result, the Identity Management is informed about the status of the request when the processing is done. The information about this is sent by GRC, by executing its Exit service (GRAC_EXIT_FROM_IDM_WS) WS call to Identity Services. Only one call is made which makes this result handling scenario more vulnerable as this call may be lost (e.g. due to network issues)

CONFIGURATION IN SAP IDM:
The configuration process consists of the following steps:
- Creating a configuration in the Virtual Directory Server based on a template.
- Importing the GRC 10.0 Provisioning Framework to the Identity Center.
- Configuring the imported objects.
**Optionally, configure the Identity Services if event based (call-back) result handling is needed. **
STEP 1: CONFIGURING VIRTUAL DIRECTORY SERVER:
The first step is to create the server configuration in the Virtual Directory Server so that the Identity Center uses access to SAP Access Control for sending access requests to perform risk analysis. The Virtual Directory Server contains a template that can be used to create this configuration.
STEP 2: IMPORTING GRC PROVISIONING FRAMEWORK
Importing the GRC provisioning framework in the Identity Center and configuring the solution makes it possible to submit requests to SAP Access Control from a provisioning solution implemented in the Identity Center.
Adding the provisioning framework involves the following steps:
- Preparing the Identity Center
- Importing the GRC 10.0 Provisioning Framework
- Importing the service jobs
- Configuring operation->Configuring the Repository Information->Performing Initial Load Job (Load data from GRC and store the data in SAP IdM specific tables for access request creation)
The GRC provisioning framework is delivered as a separate package “com.sap.idm.grc.grc10” in SAP Identity Management 8.0.
This package provides the repository type, initial provisioning processes, jobs, and scripts to perform the initial load.
The package file “com.sap.idm.grc.grc10.idmpck” is located in the folder:
<Install_folder>\Core\ConfigurationPackages\GRC Provisioning Framework.
This package com.sap.idm.grc.grc10 provides a set of internal and public processes, forms and jobs.
STEP 3: CONFIGURING THE SOLUTION
There are five different integration scenario combinations:
- Centralized provisioning with AC Validation – Risk Analysis Only process
- Centralized provisioning using polling
- Centralized provisioning using callback service
- Distributed provisioning using polling
- Distributed provisioning using callback service
CONFIGURATION IN SAP ACCESS CONTROL:
1. Activate and bind WebServices in SAP Access control – Communication setup for interaction with SAP IDM.
To Activate Webservices you need to navigate to the below path in SPRO
- Navigate to GRC > Common Component Settings > Integration Framework > Maintain Service Providers and Consumer Proxies in SOA Manager> click on Web Service Configuration
- Bind and activate the GRC WebServices for communication between SAP IdM resp. VDS and SAP Access Control.
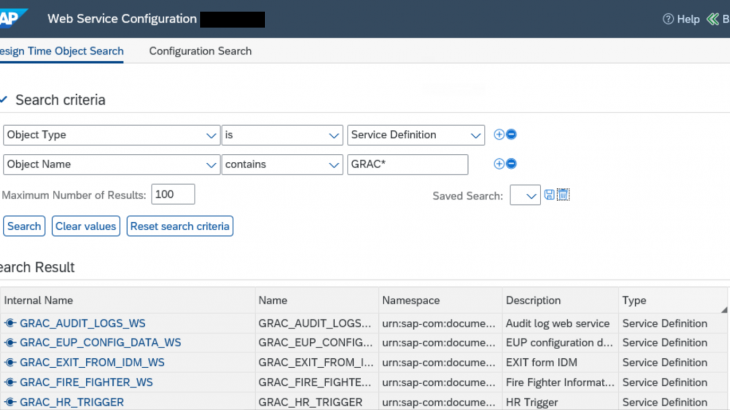
- In SOAMANAGER, look for *GRAC* web services and create configuration for each of them.


2. Maintain data for access request creation used by SAP IdM – Maintain valid data which has to be used by SAP IDM for access request creation.
The Highlighted configuration must be maintained.

3. Creating a Connector – A connector needs to be created which can be used for Callback Service and a HTTP connection,
- Navigate to Common Component Settings/Integration Framework in the structure of your GRC system.
- Start the IMG activity “Create Connectors”.
- Follow the IMG activity documentation to create a new connection of type G, i.e. HTTP Connections to External Server. You may name it e.g. NW_IDM72. The connection needs to point to the J2EE engine where the Virtual Directory Server web service (the callback service) is deployed as a target system.
HOW TO CHECK WEBSERVICES (in GRC system)
- Execute SE80 >Navigate to Repository Information System > Enterprise Services > Service Definitions
- Select Application Component GRC-AC and click on Execute
- Result is displayed with the list of all “GRC-AC” available WebServices.
- Choose one WS for testing purpose (double-click)
- Click on the “Test” Button to open Service Definition Test window
- Generate Request Template & Execute.

7. Switch to “XML editor” once the template is opened.

8. Fill in the correct test Input data (refer to the Metadata link below) and execute.
9. The response will be displayed.
**you can also execute Transaction SPROXY_START and enter the webservice in service definition and click on test**
You can check the below link to refer to the Input data required for GRAC_USER_ACCES_WS (User Access Request Service) web-service.
Metadata for GRAC_USER_ACCES_WS web service – Governance, Risk and Compliance – Community Wiki
Understanding the IdM 7.2 – GRC10 interface | SAP Blogs
WEBSERVICES IN SAP ACCESS CONTROL
Below is the list webservices used within VDS for Communication purpose that are activated


BUSINESS ROLE SYNCHRONIZATION:
The enhanced integration between SAP Identity Management 8.0 and SAP Access Control 12.0 or higher allows you to synchronize business roles between both systems before user provisioning.
When business roles are synchronized, SAP Identity Management and GRC use a shared role model. Both systems synchronize the content of the business role (privileges/technical roles) through an automated process. After that only one request for segregation of duties check is needed for the whole content of the role.