Informative Note: Created this blog to provide information on how to configure SSL manually from OS level on newly installed S/4 HANA System – ABAP and HANA DB.
My Scenario: Consider, we are having newly installed fresh S/4 HANA system Non Appliance. SSL configuration needs to be done for production purposes. All connections should be communicated via SSL only irrespective of application servers instances/count. None of the PSE files created/touched. We are going to configure SSL for the installed system from scratch. Lets go !
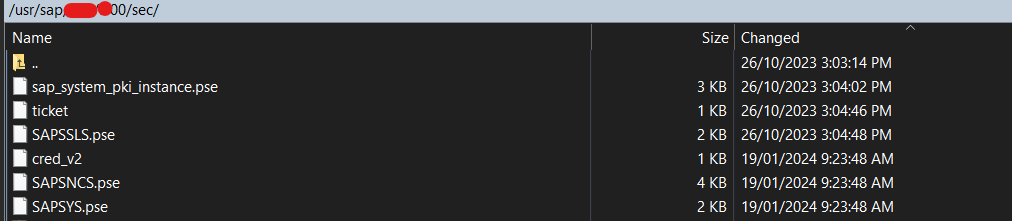
- You can see PSE files are not generated yet in STRUST. Default PSE files available by default in OS level. No SAPSSLC PSE file exist for ABAP Instance.

Prerequisites:
- Download & UNCAR COMMONCRYPTOLIB file. Place in all sec folders – ABAP/ASCS/HDB to use sapgenpse exe. [SIDADM – SAPSYS]
SSL Configuration:
- In general, To make SAP System run with SSL checks, Add below parameters in DB Environment Variables and ABAP Default Profiles.
- Additional – Just one point to remember – Consider, SSL Communication occurring between ABAP Server and HANA DB. To make ABAP to trust and establish connection, HANA DB Server, Issuer & Root CA should be imported in ABAP Server Client Standard file (SAPSSLC).
1) IN ABAP Instance Profile:
| – Check in profile- SECUDIR /usr/sap/SID/DINS/sec (It will be available by default) You can set for current session during certificate renewal as well. – Add/Change parameter to enable SSL, icm/HTTPS/verify_client = 1 [ Will do SSL checks while making communication with other systems. No impact during system start ] – To Secure ABAP and HANA DB connection, Set Environment Variable(dbs_hdb_connect_property) as well as add parameter in Default profile as a backup -dbs/hdb/connect_property =ENCRYPT=TRUE,sslCryptoProvider=commoncrypto,sslKeyStore=/usr/sap/SID/DINS/sec/SAPSSLC.pse,sslTrustStore=/usr/sap/SID/DINS/sec/SAPSSLC.pse [Used for Application <-> DB connection with SSL checks. System won’t start if SSL configuration not done ] |
Note – FYI (ADDITIONAL):
- Connection properties will be taken from profile mentioned in HDBuserstore list. By default, we would use DEFAULT Profile. Hence, We need to add all dbs parameter in DEFAULT.PFL only.
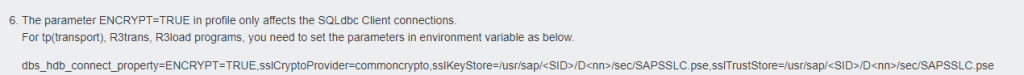
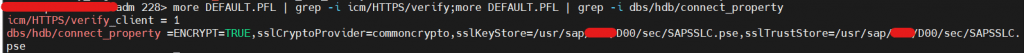
- But, for R3trans and others, we need to set Environment variables as well since adding dbs connect property parameters in DEFAULT.PFL will work from ABAP Instance (During System Start & communication especially) only.
- If SSL configured and you fail to add (setenv) environment variable, we will face “Only Secure Communication allowed” error during R3trans command. But, System will be up and running since we would have set SSL parameter dbs/hdb/connect_property ENCRYPT=true in DEFAULT.PFL
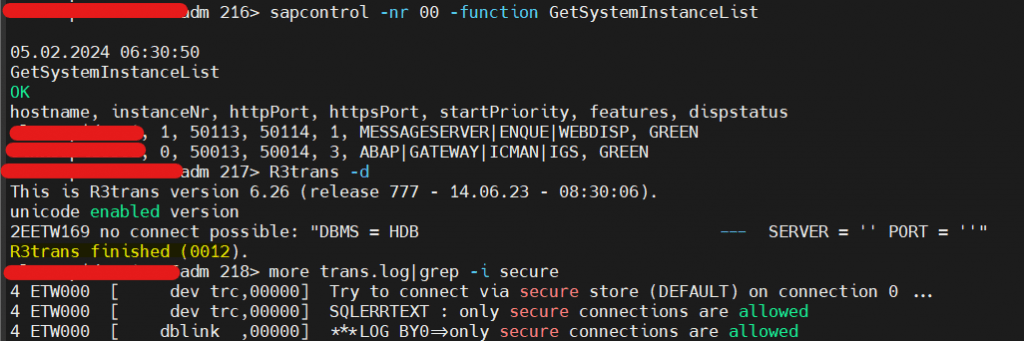
Setting Environment Variable
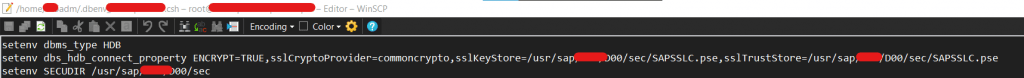
- You can use setenv command directly if you don’t face hectic issue – env variable disappears after session logout.
- I will prefer to add parameter in db env file itself -> dbenv_hostname.csh in sidadm home path. Variable name should be dbs_hdb_connect_property only since “/” not allowed. Only Variable name with Alphanumeric characters allowed. Just restart sapservice of sidadm alone to reflect changes.
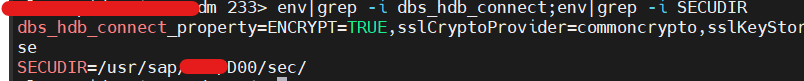
2) IN HANA – SYSTEM DB:
- Enable SSL.
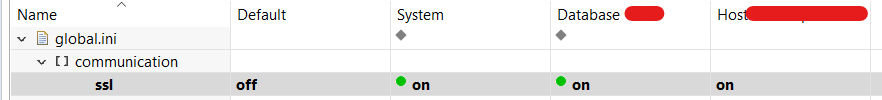

- SSL Configuration done. Now, system will start with SSL post restart.
3) Error 1 – SAPSYSTEMPKI PSE Failure – ASCS.
- Restarted system.
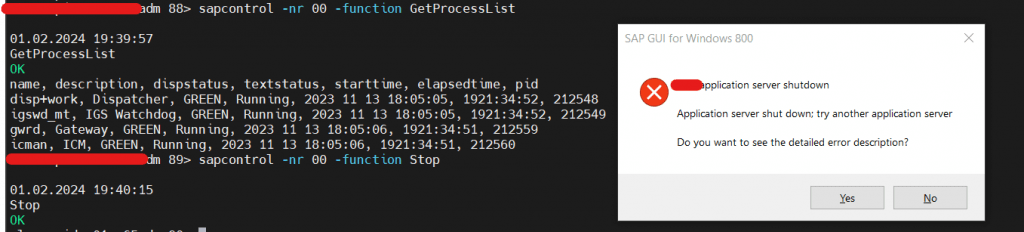
- Once restarted, Message server went down “Certificate Unknown Error – SAPSystemPKI pse”. This might be due to PSE file wrongly generated during installation. We just need to delete and recreate system PKI. This issue won’t occur mostly.
- Reference: https://me.sap.com/notes/0002629916 – Creating credential from instance PSE failed, Loading instance PSE failed or Peer not trusted
- Command -> Delete sapsystempki instance pse in all instances -> Deleted SSFS data folder -> sapcontrol -nr DINS -function UpdateSystemPKI I
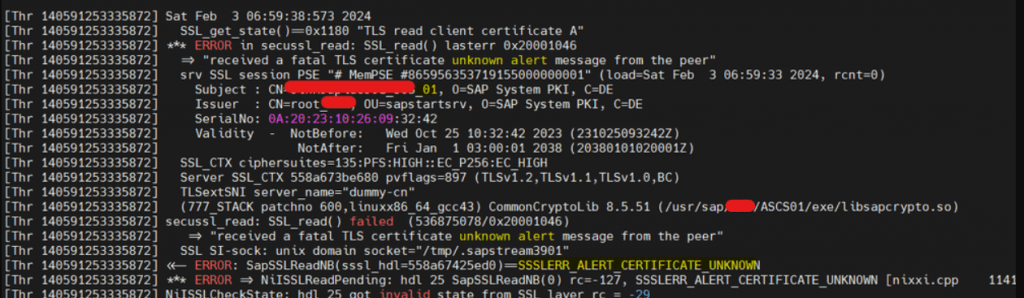
- I have recreated systemPKI instance pse file using sapcontrol command. But it unable to set PIN while starting system – Could not reset PIN for container. I have set ASCS01 SEC folder as SECUDIR for current session then restarted system which automatically updated PIN.
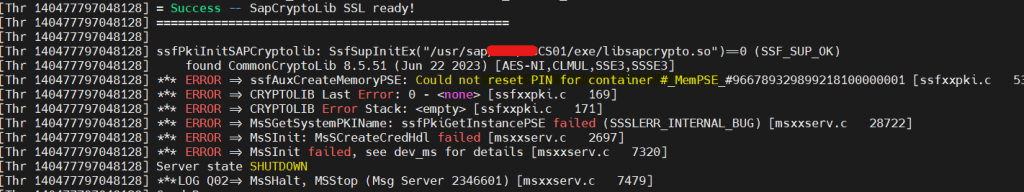
- Message server started and running fine.
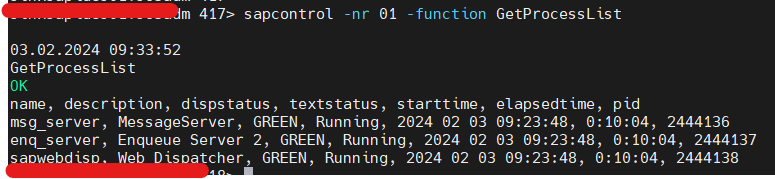
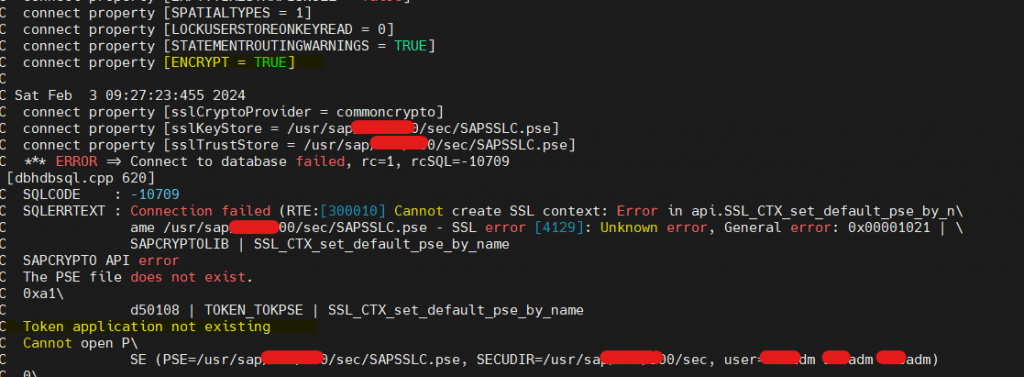
4) Error 2 – PSE FILE NOT EXIST – ABAP – SAPSSLC
- Message Server started fine. ABAP Dispatcher stopped and R3trans failed as expected since we haven’t created SAPSSLC PSE file yet.
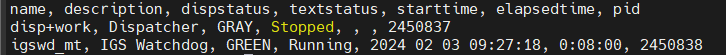
Hence, we can confirm SSL Configured for ABAP and HANA DB and it’s working fine. You can also start system and check ABAP SSL alone before adding HANA DB parameter and changing SSL enforce ON. Below snap taken before configuring SSL for HANA DB.
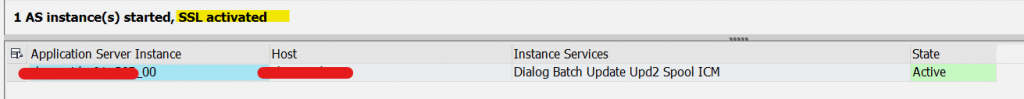
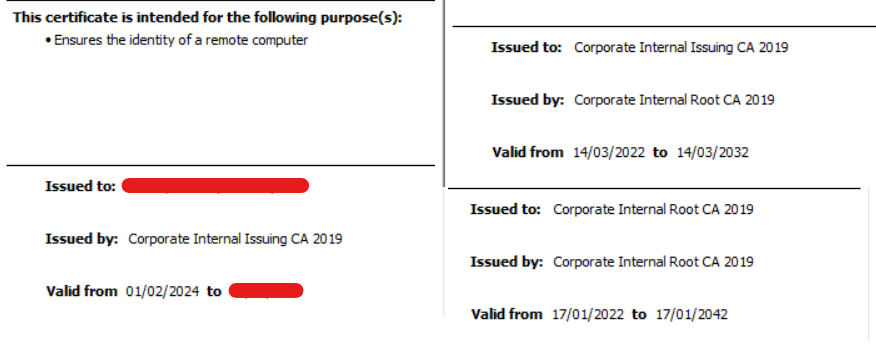
- Currently, ABAP Dispatcher and DB connectivity is in failed state. Now, we need to generate SAPSSLS,SAPSSLC PSE files for secure communication post certificate renewal. Make sure to have CN as FQDN – VM/Server Hostname.
Certificate Renewal:
- You can renew certificates on own if you request security team and get access to renew certificates. Mostly, It will be provided to all employees irrespective of the domain in most of the companies.
- Use SAP MMC or MMC Snap in – Certificates to request new certificate.
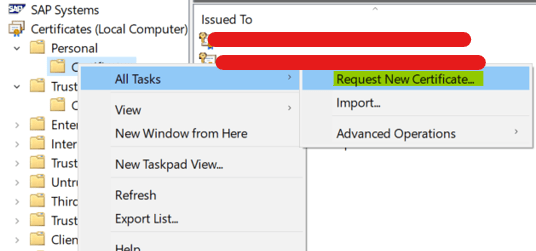
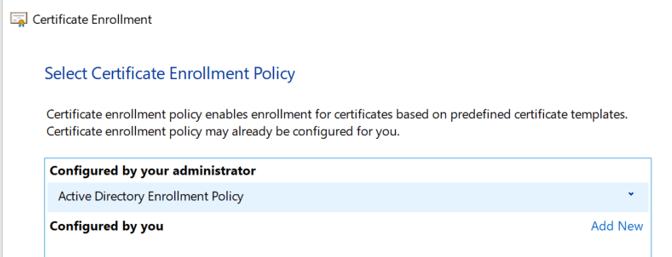
Manual Renew – For all OS other than Windows.
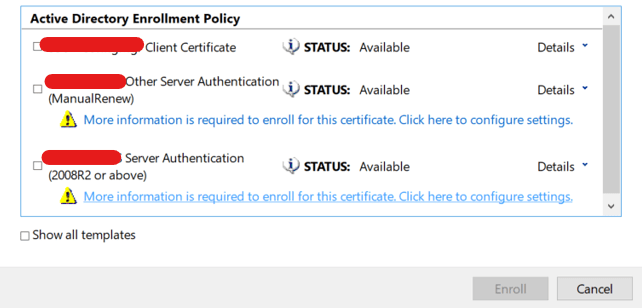
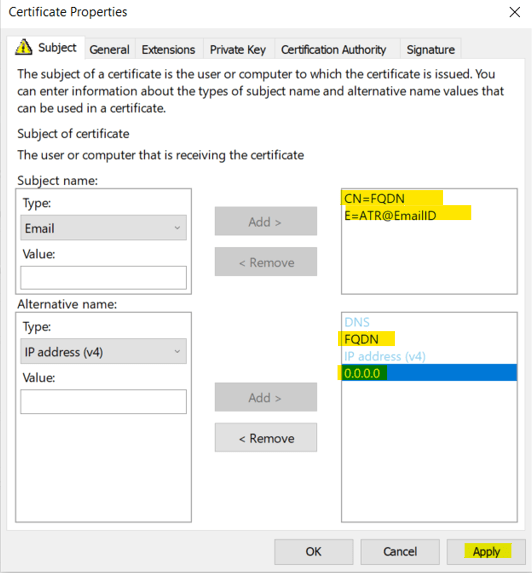
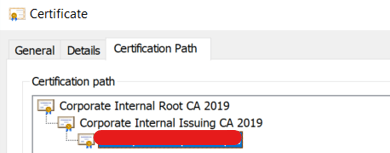
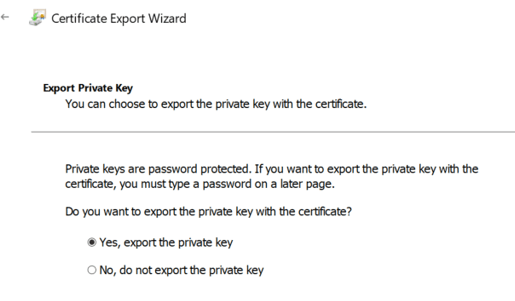
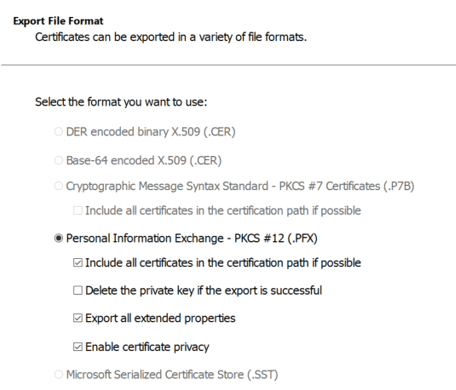
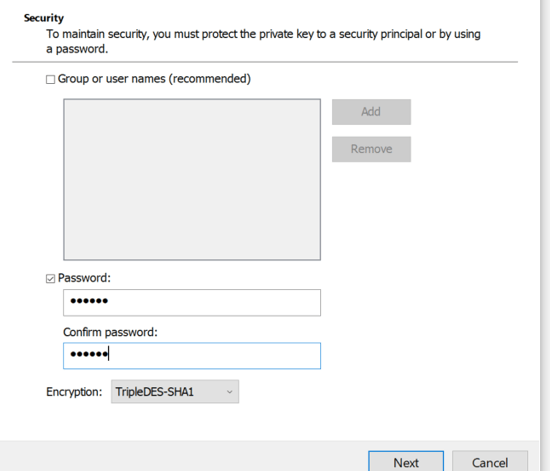
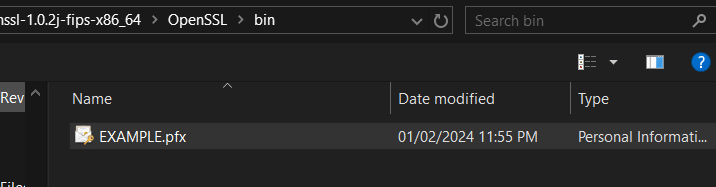
- Once pfx file exported, you can use OpenSSL to fetch Server CA, Root CA, Issuer CA, Private Key (Additional). You can also export Root CA, Issuer CA directly from SAP MMC itself. It’s global and common.
- OpenSSL will be open source software. You can surf in web and download. Link can’t be shared due to compliance.
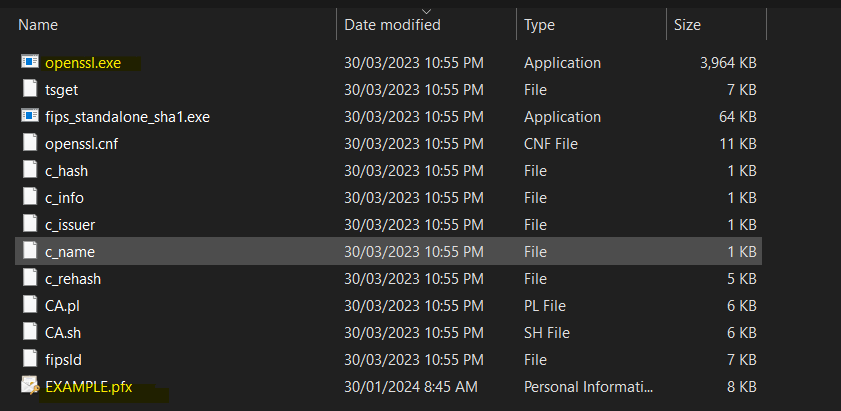
- Path -> openssl-1.0.2j-fips-x86_64\OpenSSL\bin\ – My Exported Filename from SAP MMC – EXAMPLE.pfx.
- Command to convert -> openssl.exe pkcs12 -in EXAMPLE.pfx -out EXAMPLE.txt -nodes
- Provide Private Key password and convert pfx to text file.
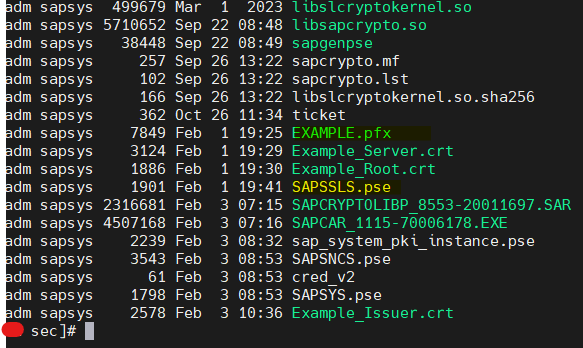
- Before generating PSE file from Pfx using sapgense. Copy your certificates and pfx files to Sec folder. [SIDADM:sapsys owner with full permission 777] Private Key certificate not required. We need to use Issuer,Root with PFX file only.
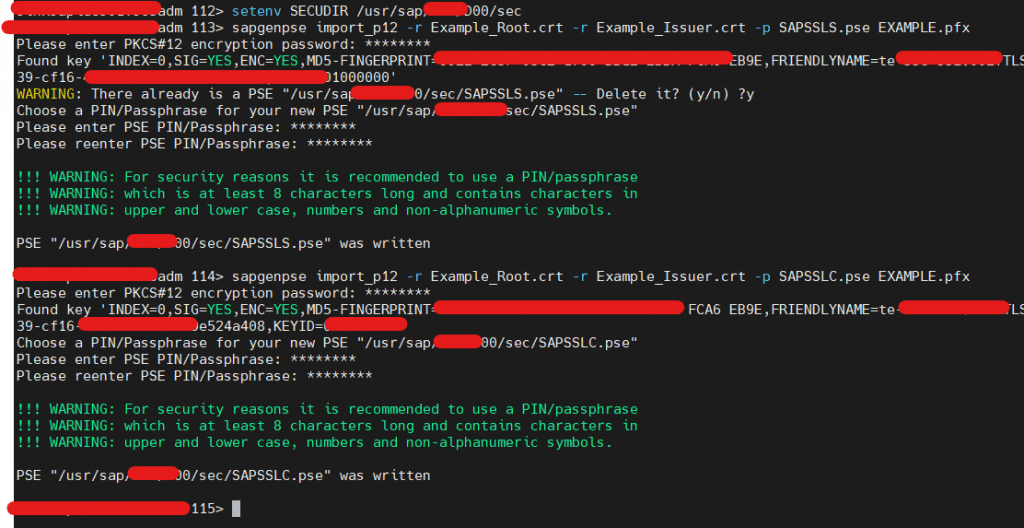
- Create PSE File with command – sapgenpse import_p12 –r RootCertificate.crt –r IssuerCertificate.crt –p <SAPSSL>.pse pfxfile.pfx
- Once SAPSSLS and SAPSSLC generated, set secure login with your provided PSE password separately. This step is mandatory to check certificates without password.
- Command -> sapgenpse seclogin -p SAPSSL*.pse
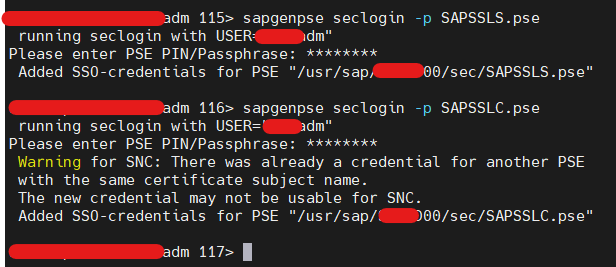
- Once seclogin set, run below command and check whether it’s fetching right certificate or not. Command -> sapgenpse get_my_name -p SAPSSL*.pse.
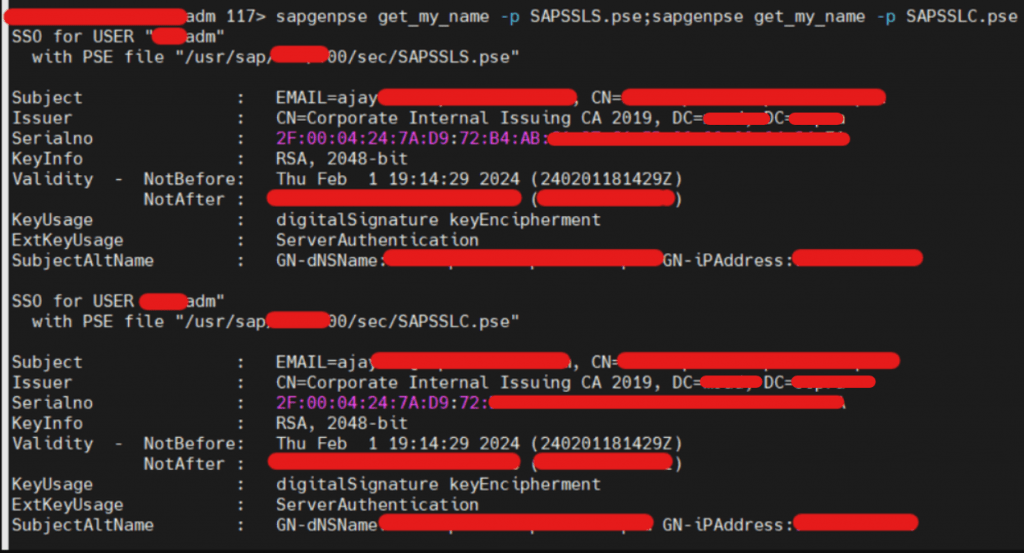
- You can also provide password manually and check certificates if seclogin not done. But it’s not recommended.
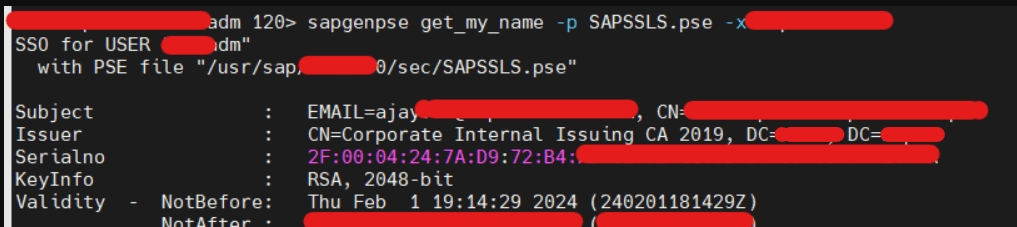
- Command -> sapgenpse get_my_name -p SAPSSL*.pse -x password
- We have renewed SAPSSLS.pse as well as SAPSSLC.pse of ABAP Instance. Check R3trans -d now.
5) Error 3 – Certificate Trust Error post SAPSSLS/C Regenerated
- R3trans failed with Certificate trust error now.
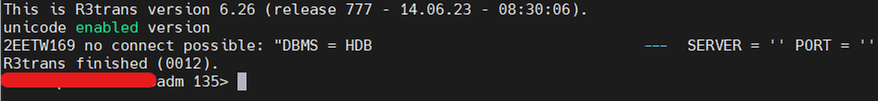
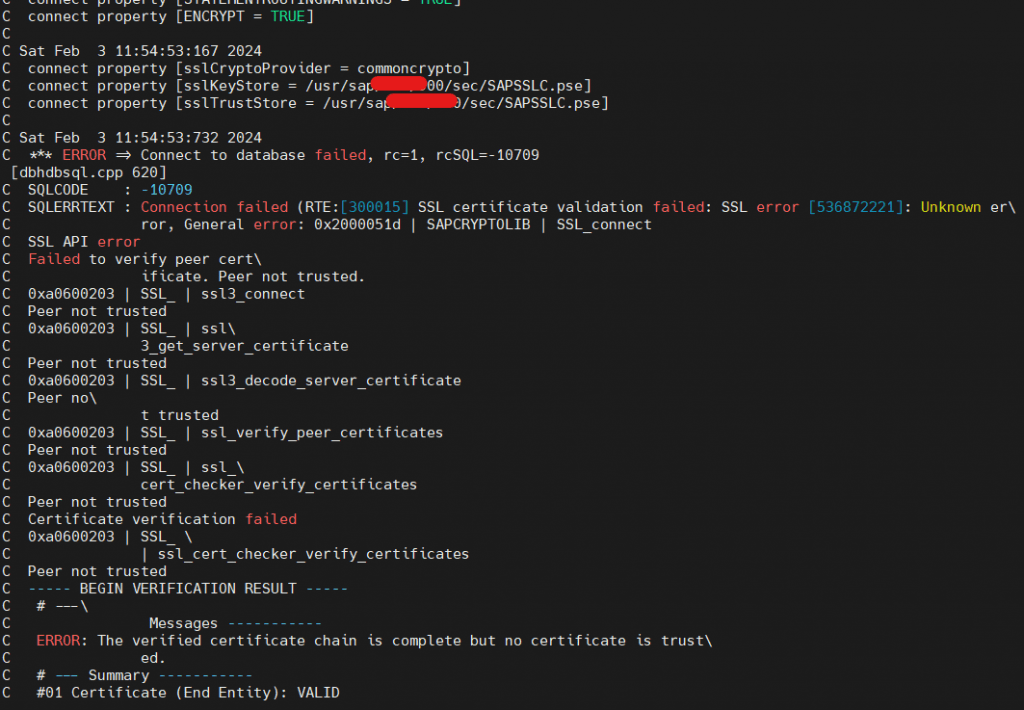
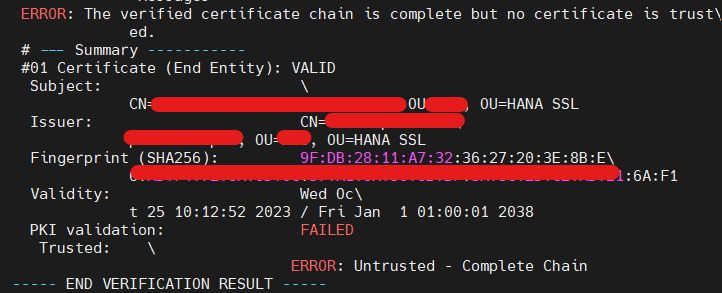
- Certificate which it’s referring is HANA DB – sapsrv.pse file certificate. A default dummy certificate with hostname.
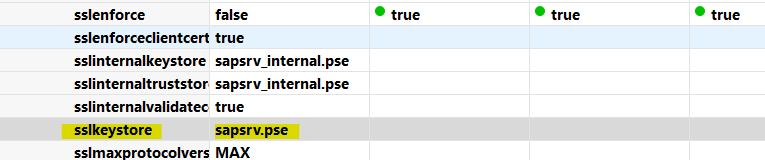
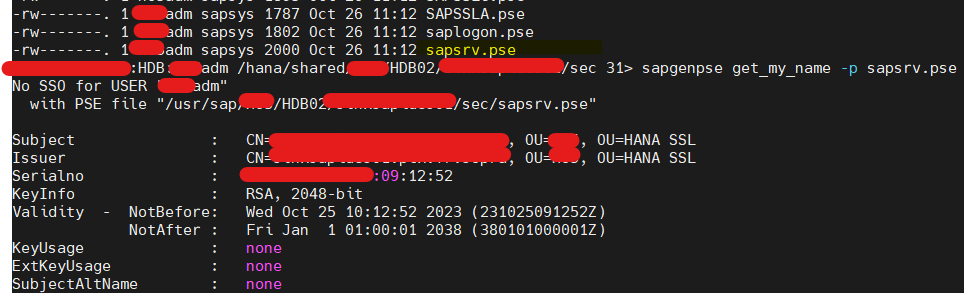
- As already mentioned, To make ABAP System to trust HANA communication, SAPSRV PSE – Server, Issuer and Root certificate should be imported in ABAP SAPSSLC which is an SSL Secure Check PSE defined in dbs/hdb/connect_property.
- There are two options to make trust.
- Either – Export currently used dummy certificate and sign with CA, then import all certificate chains in ABAP SAPSSLC pse file.
- OR – Delete sapsrv pse and use our renewed certificate itself to regenerate sapsrv.pse. I’m using our certificate only.
- Copy our certificates and pfx into hdb sec folder. Assign DBSIDADM:SAPSYS with full 777 permission. Regenerate new sapsrv.pse. [Delete old sapsrv.pse if prompt occurs]
- PKList will be empty only for all newly installed system. If any certificates exist, you can export certificate using sapgenpse command and import post regenerate.
- Command to view PKCertificateList -> sapgenpse maintain_pk -l -p sapsrv.pse
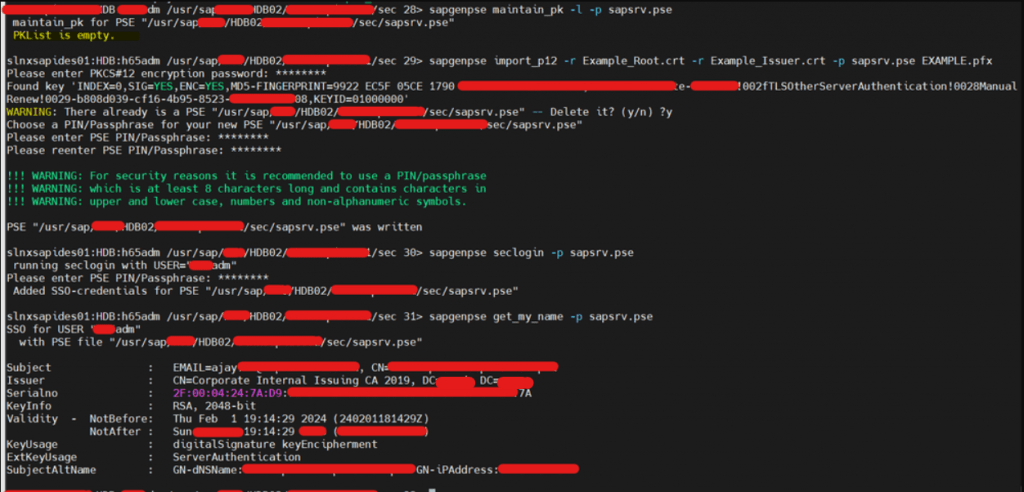
- SAPSRV pse renewed with our certificate successfully.
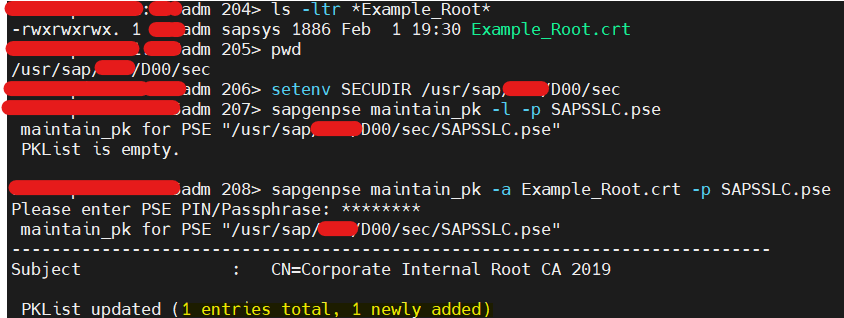
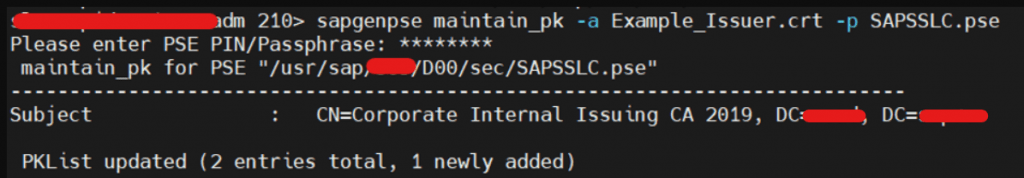
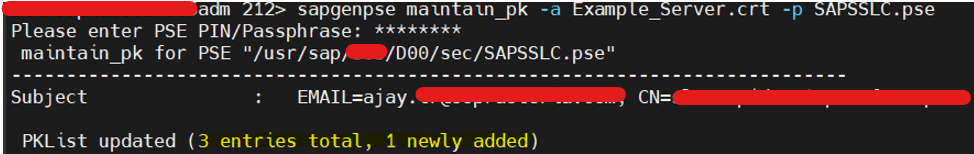
- To make ABAP Instance to trust this certificate, Import all certificate chains into ABAP Instance SAPSSLC.pse
- Command to add certificate in PKCertificateList -> sapgenpse maintain_pk -a Example_Filename.crt -p SAPSSLC.pse
- Restarting system will reflect and fetch updated sapsrv pse to connect from ABAP. Before restart, Disable SSL & SSL ENFORCE from ON to OFF then restart system. Else, you will face “Cannot create SSL Engine” Error.
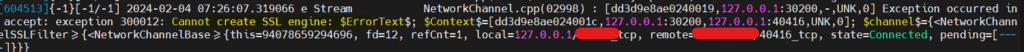
- Post restart, Enable SSL & SSLENFORCE from OFF to ON to enable SSL. Check R3trans now.
6) SSL CONFIG COMPLETED
- R3trans returns 0. APP<->DB Connectivity successful with SSL. ABAP Dispatcher also started and running fine.
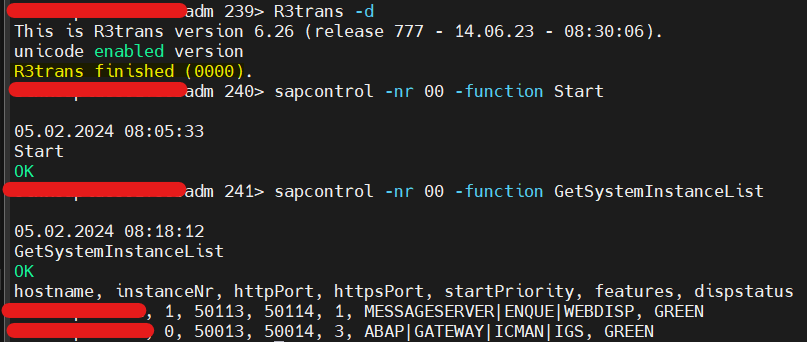
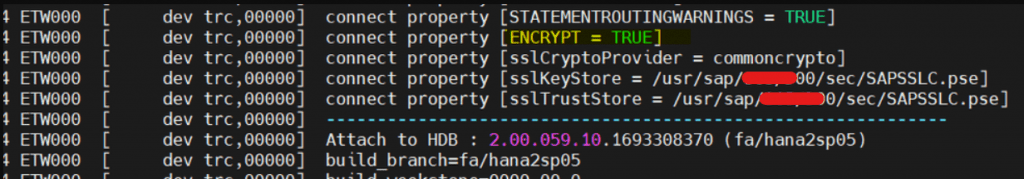
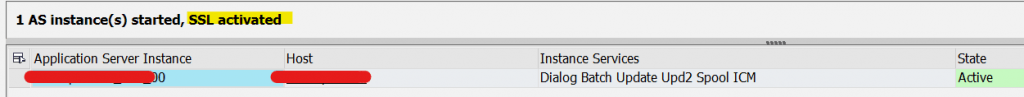
- Hence, We have setup and enable fully secure SSL for ABAP to Other systems (icm/https/verify_client) as well as ABAP to HANA DB (enforced SSL). All communications will occur with SSL checks only.
- Connection will be rejected if communication occurred without SSL.
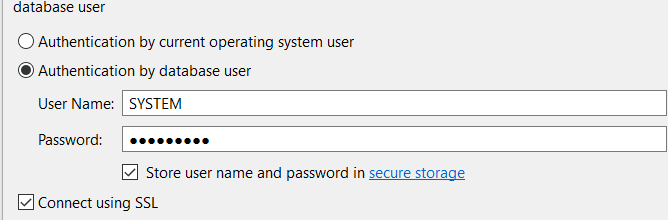
7) To connect HANA STUDIO (HANA DB) WITH SSL:
- Change Public_Hostname_Resolution from ip (default) to FQDN. If you fail to change, you will face Hostname Verification failure”. We have renewed server certificate with CN=FQDN but HANA Studio will expect CN=IP if public hostname set as default ip.
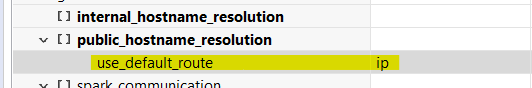
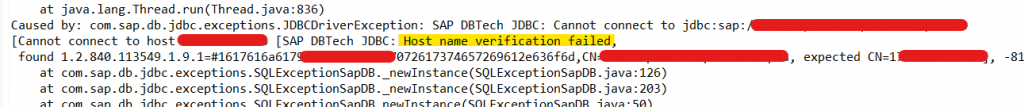
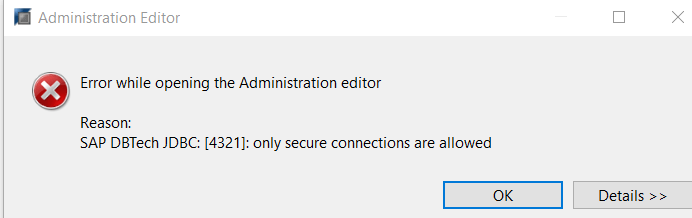
- We will be receiving error “Only Secure Connections Allowed” if we trying to connect without SSL.
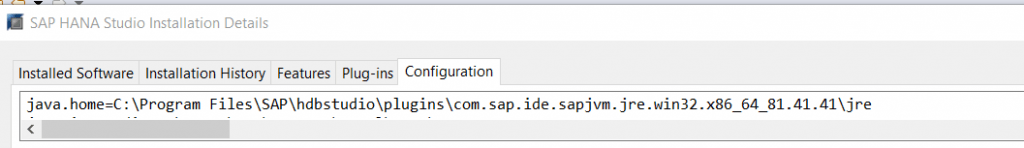
- Import SAPSRV.pse certificate in our JAVA.HOME directory of HANA Studio to establish trust.
- JAVA.HOME – C:\Program Files\SAP\hdbstudio\plugins\com.sap.ide.sapjvm.jre.win32.x86_64_81.41.41\jre\
- Certificate CACERTS path – C:\Program Files\SAP\hdbstudio\plugins\com.sap.ide.sapjvm.jre.win32.x86_64_81.41.41\jre\lib\security\cacerts
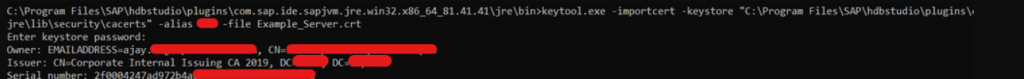
- Keytool executed from jre\bin path. Server certificate saved in the same path.
- Command (Run as Administrator): keytool.exe -importcert -keystore “C:\Program Files\SAP\hdbstudio\plugins\com.sap.ide.sapjvm.jre.win32.x86_64_81.41.41\jre\lib\security\cacerts” -alias SID -file Example_Server.crt
- Default cacert password will be “changeit”
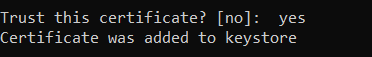
- Restart HANA Studio and Add system. Now, You can able to connect HANA DB with SSL.
Why OS LEVEL INSTEAD OF ABAP STRUST?
- Above configuration will be helpful (permanent) if PSE file corrupted/collapsed/distribution failure from STRUST/Certificate Expired and System went down.
- We can manually renew certificates from OS level and bring system up. Once system up, we can import same renewed certificates in STRUST and distribute to save it in OS level as well.
- STRUST -> PSE -> IMPORT -> SELECT PFX File
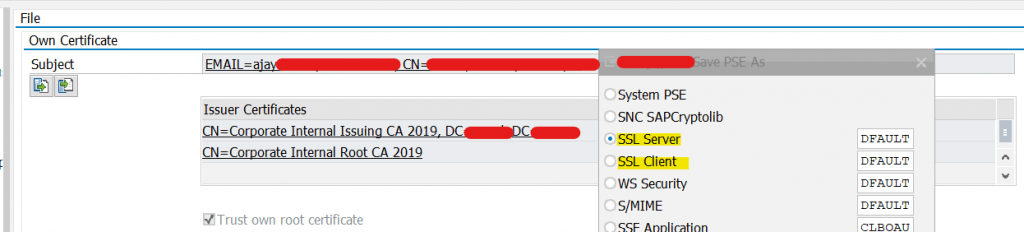
- Do for SAPSSLS, SAPSSLC, SAPSSLA. For SAPSSLC, Import Server, Root & Issuer CA of SAPSRV.pse in certificate lists. Else, ABAP<->DB connection will fail post restart. Distribute using PSE -> Distribute All.










