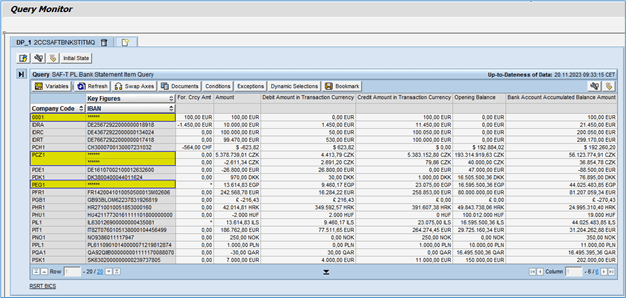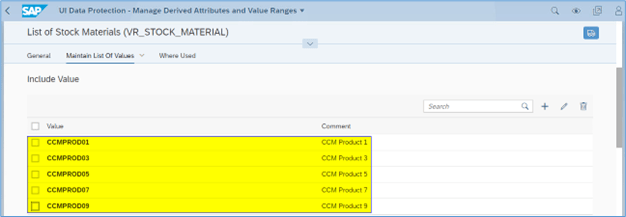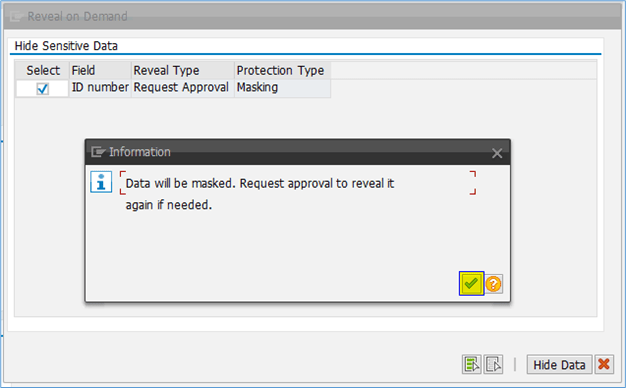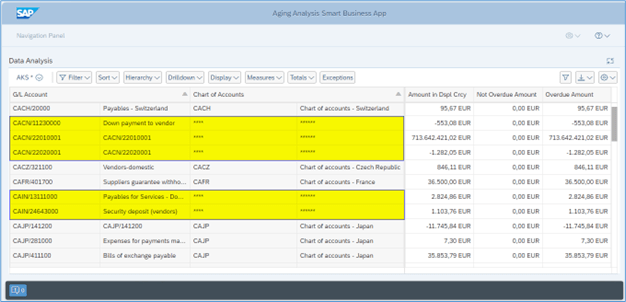
Introduction In this blog, we will learn how to mask Chart of Account field information based on G/L Account field information of Aging Analysis Smart Business app Analytical Query. Analytical Queries are used for reporting and analysis. Chart of Account field information of Aging Analysis Smart Business app Analytical Query need to be masked where […]