SuccessFactors takes great strides to ensure security and data privacy for all our customers, no matter where they are located or do business.
This blog will address the specific regulations that apply to both the European Union and Canada, and how SuccessFactors not only follows these regulations, but more often than not, go beyond them. As you read this, keep in mind that SuccessFactors is considered a sub-processor. This means that we do not collect information about the employees of our customers – we only store and process data provided to us by our customers based strictly on their instructions.
Adhering to Strict Regulations from the EU, Canada, and the U.S.
To protect the data for our customers that are based in Europe and Canada, we continually follow any legal or compliance regulations from these countries. We combine them with additional ones from the U.S., and from there, we formulate our security policies.
Here are a few of the key ones that have influenced our policies.
- European Union (EU) Data Privacy Directives. The European Union (EU) Data Privacy Directives is an overarching set of requirements where each country, or member state, is allowed to implement their own interpretations and requirements for data privacy laws. Because of this, SuccessFactors is obligated, as a cloud vendor providing service to multiple states, to address the requirements of each member state.
- British Standard 10012. To ensure the greatest security and to meet each country’s requirements, we looked at the state-to-state requirement and adopted the most stringent. We use the German privacy law (which is based on, among other things, the Federal Data Protection Act) as the baseline. This is the most stringent of all European laws and it, in turn, is based on the British Standard (BS) 10012, the only international standard for data privacy. So essentially, we are using the BS 10012 as a standard. Two of the most salient points of the standard are that corporations should commit not to take or use customer data unless absolutely necessary, and to inform customers exactly how and under what circumstances their information will be used. To ensure our compliance with this and other EU requirements, we use the internationally accepted attestation standard of SSAE16 SOC2 from the Auditing Standards Board (ASB) of the American Institute of Certified Public Accountants (AICPA).
- ISO 27002. We also combine the BS 10012 with the ISO 27002 standard for our security, and audit against the combined regulations to protect our international and domestic customers fully. This standard outlines hundreds of potential controls and control mechanisms, with established guidelines and general principles for initiating, implementing, maintaining, and improving information security management within an organization. The actual controls listed in the standard are intended to address the specific requirements identified via a formal risk assessment. The standard is also intended to provide a guide for the development of organizational security standards and effective security management practices and to help build confidence in inter-organizational activities. To ensure that we have the best data security possible we have not only combined the standards to drive out all of the requirements for our program but we also audit against them and provide a written audit report for full transparency.
- U.S.-EU Safe Harbor (and Article 29 Working Party). To bridge the differences in how Europe and the U.S. protect privacy, the U.S. developed the U.S.-EU Safe Harbor framework. One of the EU’s directives is that no data can be transferred to a non-European Union country that didn’t meet the EU’s data privacy requirements. The Safe Harbor program requires companies in the U.S. address the requirements of the EU’s data privacy laws. This is primarily a self-regulating framework. Since this was set up, an advisory group to the European Commission called the Article 29 Working Party has advocated for “the protection of individuals with regard to the processing of personal data and on the free movement of such data.” The advisory group wants companies to validate the controls that are in place that support the concept of safe harbor. Ultimately, however, the responsibility is on the customer, or the company that controls the data, to validate itself and all of its sub-processors. Interestingly enough, Germany does not recognize Safe Harbor regulations in the same way as other EU states. It requires all parties involved in data transfer to assure that Safe Harbor requirements are met in a more formalized and structured manner. This is important for German-based businesses using U.S. cloud service providers since the providers must take additional measures to ensure compliance. Because SuccessFactors is a sub-processor of data, we’ve taken the proactive approach to our delivery and audit our infrastructure to validate the Safe Harbor controls.
- Patriot Act. Another concern for our European customers is the Patriot Act. We are often asked if we would allow the U.S. government access to any customer’s data because of this act. The regulation is an acronym for Uniting (and) Strengthening America (by) Providing Appropriate Tools Required (to) Intercept (and) Obstruct Terrorism. The Patriot Act is all about terrorism, and even with this in place, the U.S. government is not permitted to ask for disclosure of data without a subpoena warrant, or a writ from a judge. As a cloud provider, therefore, we do not have to voluntarily provide data to a government organization, but we are obligated to follow the Patriot Act if terrorism is in question. Furthermore, there are mutual agreements and treaties for information disclosure between countries – including between the U.S. and Canada, and the U.S. and the European Union. If a specific country were investigating a terrorist act, they would go the country of origin and its government – not SuccessFactors – to exercise search and seizure rules. For instance, if the U.S. government were investigating a Canadian, they would go to the Canadian government, who would exercise its rights to seize data and use it for an investigation. However, the reality of HR data being seized in a terrorist investigation is very low. The chart below has more information on what various governments require.
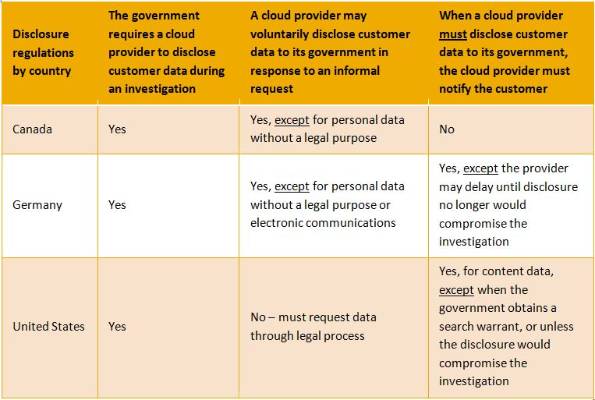
- PIPEDA. For the most part, our initiatives mentioned above will provide the appropriate safeguards to our Canadian customers. In addition, Canada has implemented PIPEDA, or the Personal Information Protection and Electronic Documents Act to promote consumer trust in electronic commerce. This act is also in place so that Canada can reassure the European Union that the Canadian privacy laws are adequate to protect the personal information of European citizens. One of the requirements of PIPEDA is a “comparable level of protection.” This means a third-party processor, such as SuccessFactors, must provide protection that can be compared to the level of protection the personal information would receive if it had not been transferred. SuccessFactors has policies and processes in place to ensure that the information in its care is properly safeguarded at all times. However, PIPEDA does not prohibit organizations in Canada from transferring personal information to an organization in another jurisdiction for processing, nor does it distinguish between domestic and international transfers of data.
- Canadian Anti-Terrorism Act. This was passed in 2001 and has a number of investigative processes similar to those found in the U.S. Patriot Act.How we manage data in EuropeIn addition to questions about the above regulations, our European customers often ask us how we manage data. We are contractually obligated to disclose how we manage our data, and as mentioned above, we are set up as a sub-processor, or a data processor. We are not a data controller, so we have no rights or warrants to the data, which always belongs to the customer. We’ll only execute what is legally permissible under each individual customer contract.
Success Factors has a “defense in depth” approach to not only secure the data, but also to ensure the privacy of the data for our customers. We have safeguards on our servers that include a host-based intrusion detection system.
As to third-party access, we have gone through our entire support infrastructure, and delineated sub-contractors from sub-processors, as prescribed by the European Union. Like the EU, we define a sub-contractor as someone that may do work for us but has zero access to customer data; a sub-processor may have potential access to customer data. For our sub-processors, we ensure that they follow the Safe Harbor framework and often include European model clauses in our contracts to make sure we are legally permitted to use them as a sub-processor.
We also audit our sub-processors every year and log any changes. We bring in third-party auditors from the outside to perform an SSAE 16 SOC 2 audit twice a year, and then provide the customer with a full 300-page report on the results of that audit.
Our European customers are also concerned with where the data is hosted as well. SuccessFactors has built two data centers in the European Union, along with all of the supporting processes. The data centers are ISO-certified and our data center in St. Leon-Rot, Germany, is a tier-four data center.
Our data is encrypted on disc, both back-ups and live data, so if someone were to take a disc out, the data is encrypted with AES encryption – a minimum of 128 bit – and they will not be able to do anything with it. The data is stored only in Europe and is not transferred out of Europe by SuccessFactors to be stored or processed elsewhere. Customers have the option to choose support staff from inside Europe and thus maintain European continuity within the support process; however, no data center employee has access to data. We have also implemented the appropriate internal legal agreements to provide support for our European Union and Canadian customers from within each of our subsidiaries.
As you can see, our security policies run deep and protect all our customers and their data around the world.









