In my last blog, The Best Security for Your Cloud Part 1: Unique Multi-tenancy and Defense in Depth, I discussed how SAP uses a “defense-in-depth approach” to security in the cloud. Today, I’d like to continue that discussion specifically around the Software-as-a-Service (SaaS) model and address some security issues that typically arise for companies exploring the use of SaaS applications.
In cloud computing solutions, information security and data protection issues are intensely debated and examined far more critically than on-premise solutions. This is because organizations are afraid they will lose control of their data once it moves to the cloud. Cloud vendors must, therefore, take reasonable precautions to protect their customers’ data, such as personal information, from loss, misuse, unauthorized access, disclosure, alteration, and destruction. These vendors should also take reasonable steps to ensure that the data is reliable – meaning, that it is accurate, complete, and current – for its intended use. The SAP Cloud portfolio addresses all these issues, as you will see below.
SAP Cloud: Controlled and Secure
SAP Cloud provides the security measures and transparency that build customer trust while controlling data privacy through the services in the SAP Cloud portfolio. Where your data is stored and backed-up is transparent. How it is secured at all times, and who can access or process data at all different layers at any given time, and for what purposes is also transparent.
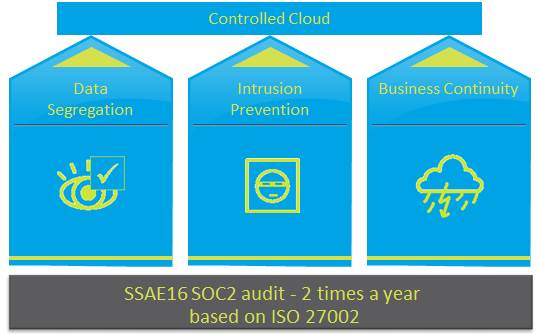
Data segregation and encryption
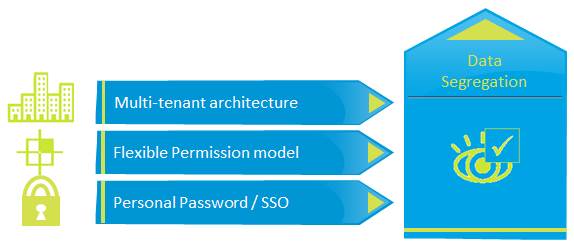
One of the reasons SaaS is so affordable is because this model is built on multi-tenancy, which primarily differentiates it from the application service provider (ASP) model or from in-house applications. For instance, with SaaS, just one software instance can serve many customers (or tenants). But this multi-tenancy raises questions about security, and in particular, around identity management, data storage location, systems operations, and data transmission and flow controls. The multi-tenant delivery and application architecture found in SAP HCM cloud solutions ensure data privacy for customers around the service as well as within the service
On top of that, strong data encryption at all relevant layers, as well as advanced infrastructure protection, ensures that unauthorized users are kept away from the protected data.
Enforcement
To comprehensively protect data, it is important to not only protect it from unauthorized access from outside the cloud, but also from inside the service. In this manner, only provisioned users can access data based on their assigned roles and associated permissions as determined in a company’s security policy. SAP Cloud has established intercompany agreements internally that permit us to manage data using all of our resources globally. All of our contracts with our sub-processors include appropriate provisions to ensure that everyone adheres to all data privacy requirements.
Full confidentiality, integrity and non-repudiation
Below you’ll find some of the other security requirements of the SaaS model and information on how the technology in SAP Cloud responds to these questions and secures up the cloud for SAP customers.
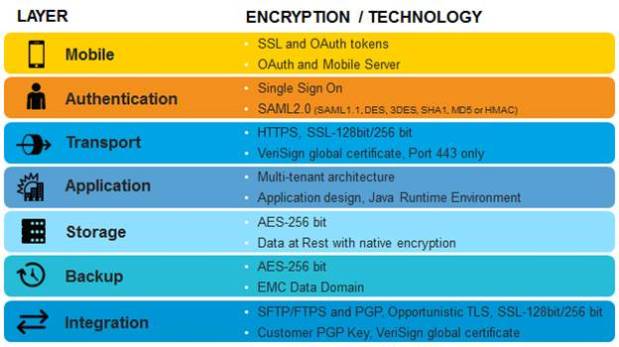
-> Identity management. Modern SaaS architecture usually involves a Web-based application and communication that occurs over the Internet. To protect identities, the communication between customers and cloud solutions from SAP leverages Secure Sockets Layer (SSL) or Transport Layer Security (TLS) encryption. Our solutions also support dedicated encrypted communication channels (WAN and VPN) for better access and integration.
And with cloud solutions from SAP, companies have a choice: they can let us manage security from top to bottom, or they can integrate SAP Cloud with their own industry-standard identity management solutions. Our solutions also include high-level security measures for internal authentication, federated authentication (single sign-on), separate authorization and authentication modules, and password protection.
-> Data storage and location. In an ASP model, each customer has unique hardware that keeps data segregated at all times. In a SaaS model, heterogeneous data may reside within a single instance of a database. To address information privacy concerns, cloud solutions from SAP provides a logical isolation within our SaaS applications that extends down to the virtual server layer. In certain environments like the SAP HANA Enterprise Cloud, companies can also use physical isolation via dedicated SAP HANA database servers that reside in dedicated customer network segments (VLANS).
In addition, cloud solutions from SAP segregate heterogeneous data by using such measures as unique databases schema, dedicated databases servers, encrypted data storage, stateless web and application tiers, and movement of data controls.
– > System operations. SaaS providers must ensure that the general capabilities of a secure and stable IT operation comply with industry standards and technology best practices. This is achieved by international- and country-specific certifications such as ISO27001, ISAE3402, and SSAE16. In some cases, industry-specific regulations and certifications are required to ensure that a cloud solution is as secure and compliant as those on premise.
Cloud solutions from SAP help organizations meet these requirements by providing industry-standard certifications and ITIL-based operational processes that include specific security management and governance functionality. This functionality includes such processes as change and security patch management, security incident management, and identity management. Cloud solutions from SAP also include configuration management, activity logging and vulnerability management, asset management, system lifecycle management, virus and malware protection, and network isolation.
-> Data transmission and data flow control. SaaS uses the public Internet to transmit data, requiring that transmission security, such as Secure Sockets Layer (SSL) and Transport Layer Security (TLS), be designed into the system. The use of SSL and TLS creates secure tunnels for information transmissions. Unfortunately, the use of distinct communication channels for each customer is counterintuitive and costly, and can become a maintenance challenge. Therefore, the use of private lines should be avoided, and instead, service providers should focus on controls.
Within the SAP Cloud portfolio, there are solutions that use dedicated WAN connections between customers and SAP. These connections may include any of the following: an SSL solution, a VPN tunnel based on Internet Protocol Security (IPsec), or encrypted router communication over the Internet, the VPN or the WAN connection. Cloud solutions from SAP also include functionality that prevents eavesdropping, tampering, and forgery through cryptographic controls, a defense-in depth strategy, and the enforcement of the following security requirements: confidentiality, integrity and non-repudiation.
Within the SAP Cloud portfolio, the controlled cloud approach guarantees that there is transparency in process, trust in management, and attestation though audit. We provide the measures and transparency necessary for the customers to trust us and keep control of their data.
There is much more to the story of how SAP is providing security for the SaaS model. To learn more, download this white paper entitled, SAP Cloud: Focusing on security so you can focus on business.
Next Part: The Best Security for Your Cloud Part 3: How We Address Data Security in Europe and Canada