I will explain how to automatically install SSL certificates on CPI using SAP’s APIs.You can follow the steps below to set a timer and have it loaded automatically, without having to manually check whether it has expired or not.
Automatically update system certificates before they expire with SAP CPI and Groovy (openssl command)
Instead of manually updating the certificate, we can automatically install the certificate before it expires with this API created by SAP.
You can use CPI APIs to update a certificate in Keystore.
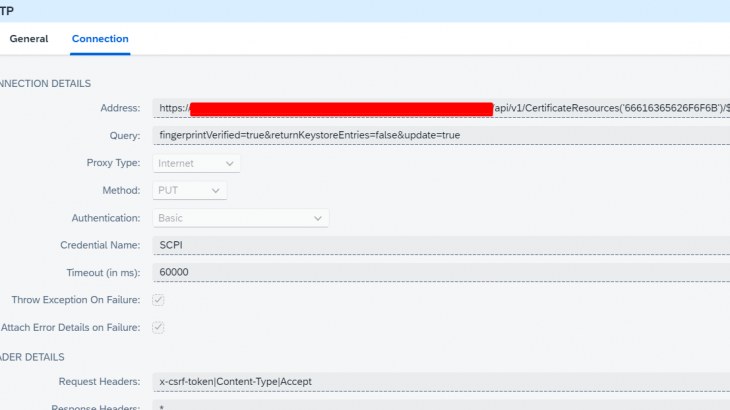
In this scenario, we will perform a PUT operation to the /CertificateResources path of the CPI API below.
| Method | Resource Path |
| PUT | /CertificateResources(‘{Hexalias}’)/$value |
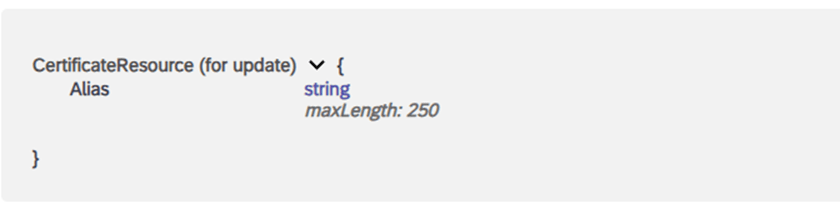
We must convert the name (alias) of the certificate we want to update in CPI KeyStore to hexadecimal.
In this scenario, we will update the certificate for facebook
hexadecimal value for facebook: 66616365626F6F6B
Note: For hexadecimal format, you can use text to hexadecimal converter online.
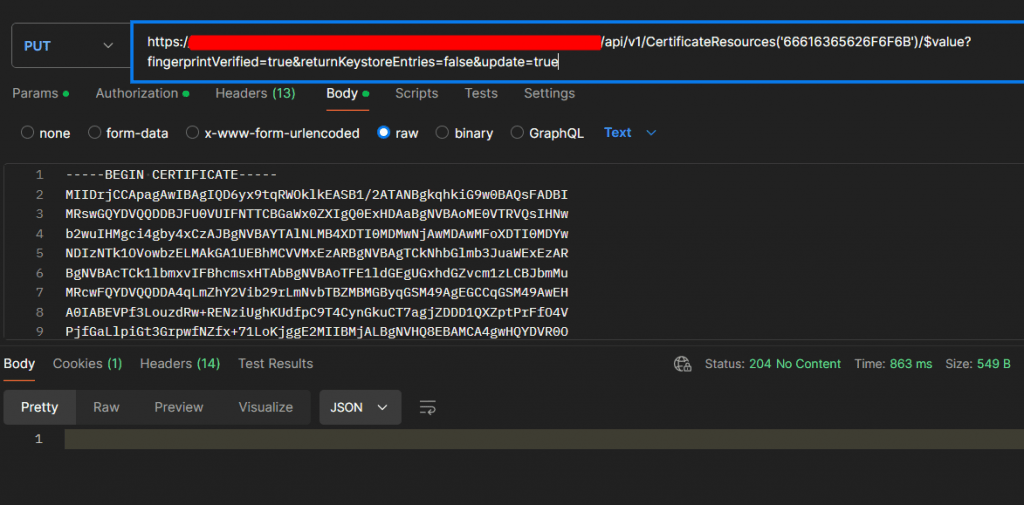
The URL to be sent in the put operation:
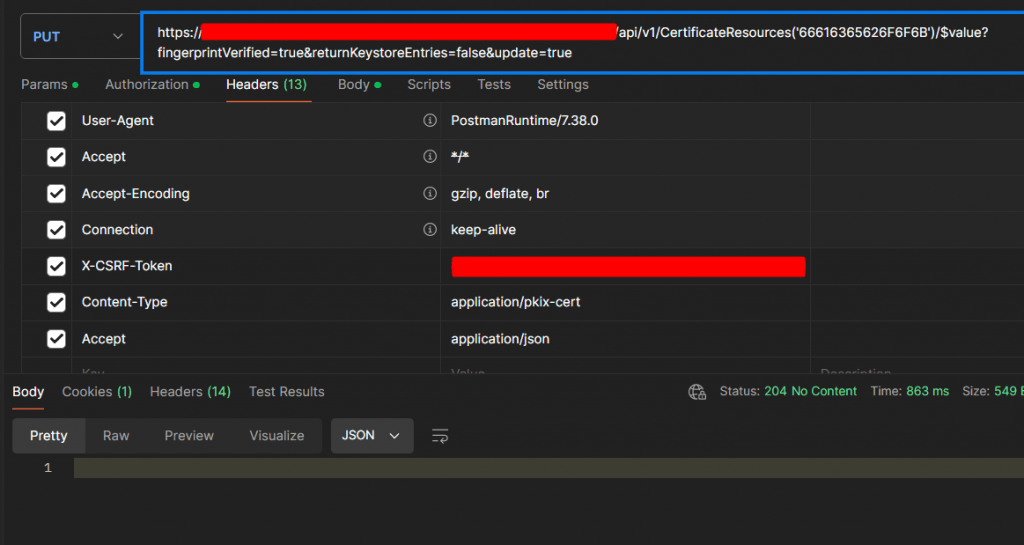
https://<host address>/api/v1/CertificateResources(‘66616365626F6F6B)/$value?fingerprintVerified=true&returnKeystoreEntries=false&update=trueWhen you test the service with the hexadecimal value in Postman, you can manually import and update the certificate.
The current content of the certificate is written to the Request Body:
For Example:
[---Begin Certificate----]
AHcAdv+IPwq2.....
.....
.....
1tIQYIeaHKDHPA==
[---End Certificate----]Header, Params and Body fields are defined as in the service document.
Header:
Request Body:
We will now do the same operation we did manually in Postman in CPI using SAP’s API.
The steps to be taken in CPI for this process are as follows.
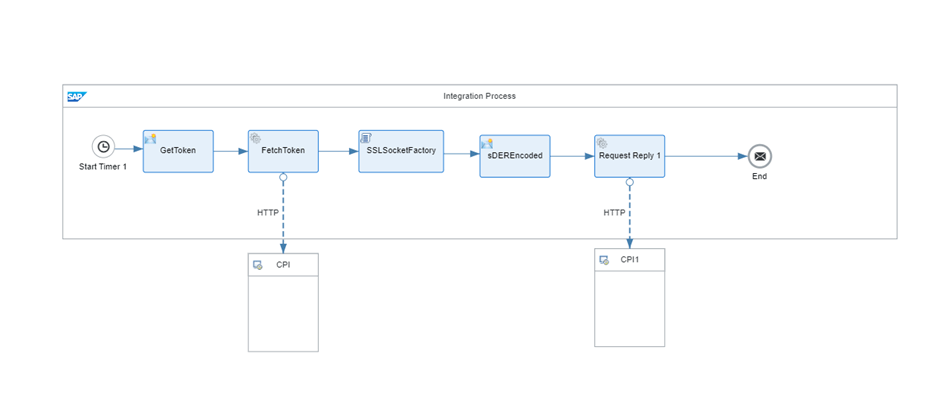
First, we get FetchToken to log into CPI.
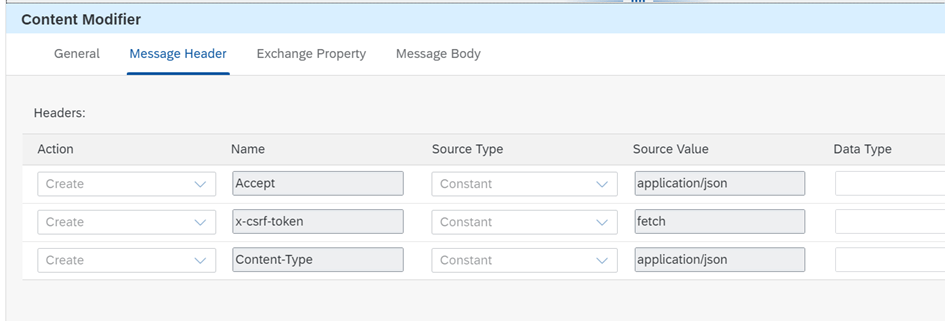
We write the following information for Get Token.
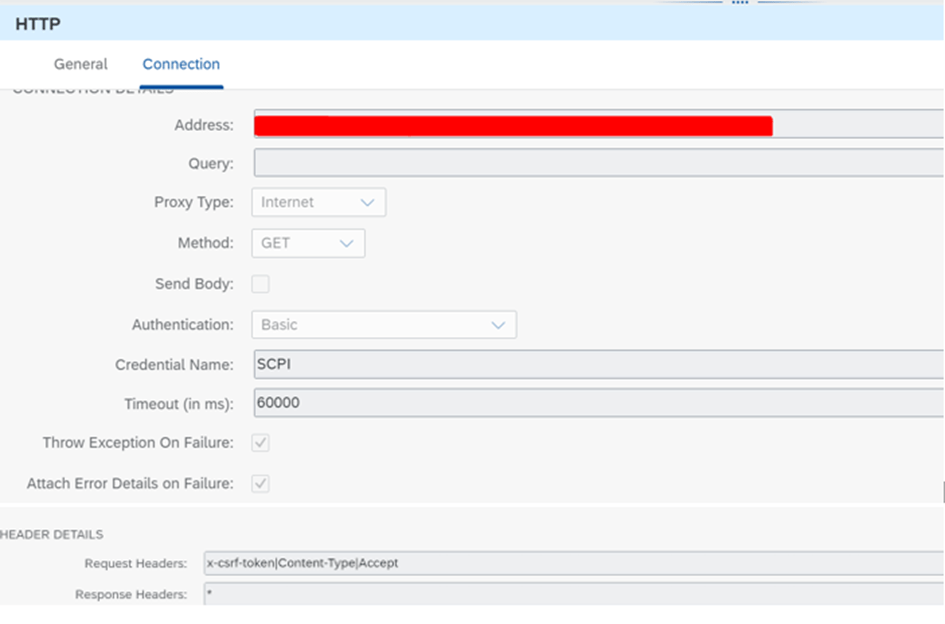
A user authorized in CPI is defined and the CPI link is written in the Address field.
In the next step, we will check the SSL/TLS certificate of the server named ” graph.facebook.com ” with groovy and obtain the current certificate.
Code detail is as follows:
import java.security.cert.X509Certificate
import java.util.Base64
import javax.net.ssl.SSLPeerUnverifiedException
import javax.net.ssl.SSLSession
import javax.net.ssl.SSLSocket
import javax.net.ssl.SSLSocketFactory
import com.sap.gateway.ip.core.customdev.util.Message
def processData(Message message) {
try {
def factory = SSLSocketFactory.getDefault() as SSLSocketFactory
def socket = factory.createSocket("graph.facebook.com", 443) as SSLSocket
// Connect to the peer
def session = socket.getSession()
X509Certificate cert = session.peerCertificates[0] as X509Certificate
def sDNName = cert.issuerDN.name // Server's DN Name
def sDEREncoded = Base64.getEncoder().encodeToString(cert.encoded)
// Set Properties
message.setProperty("sDNName", sDNName)
message.setProperty("sDEREncoded", sDEREncoded)
return message
} catch (SSLPeerUnverifiedException e) {
throw new Exception("graph.facebook.com did not present a valid cert.")
}
}Then we add a new content modifier.
Header details:
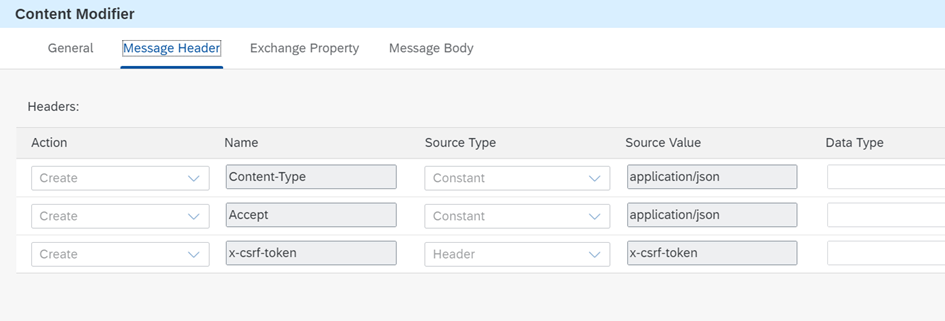
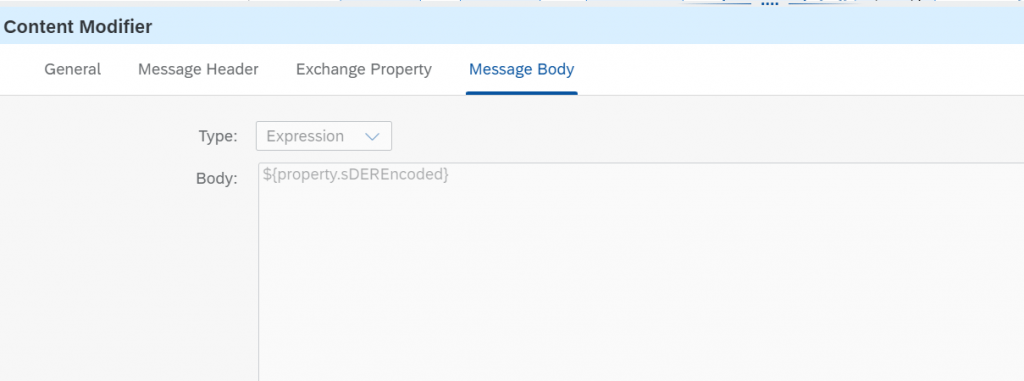
We store the certificate we received in our body.
Put service details as follows:
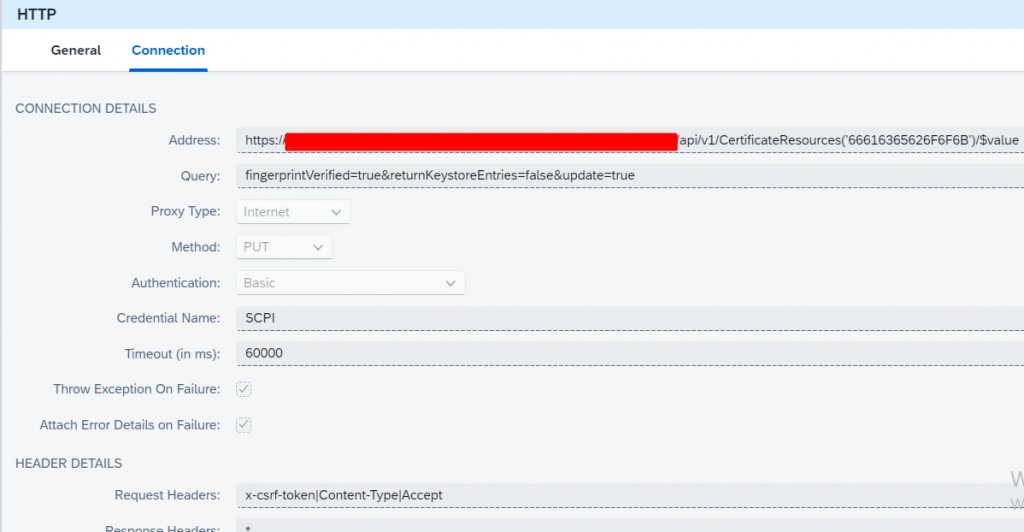
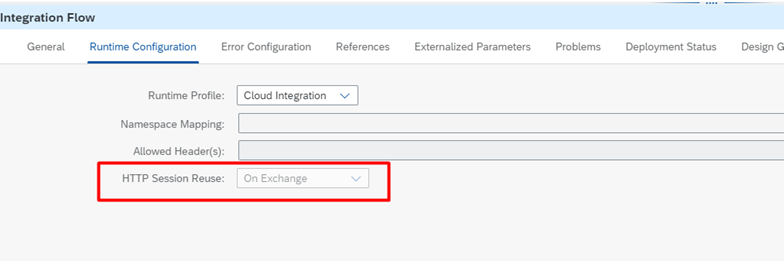
The part that should not be skipped here is; Http Session Reuse option should be On Exchange.
This option enables Http session reuse. More than one message can be exchanged with one http session. Since there will be no re-authentication in the second message, subsequent calls will be made faster.
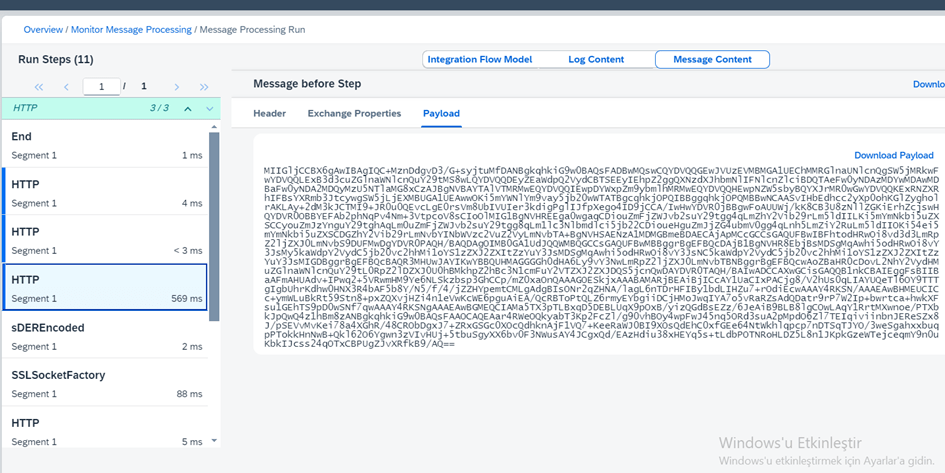
After saving and deploying the integration, we can view it from the logs.
In the following section, we write the sDEREncode of the certificate to the body and thus the certificate in the keystore is updated.
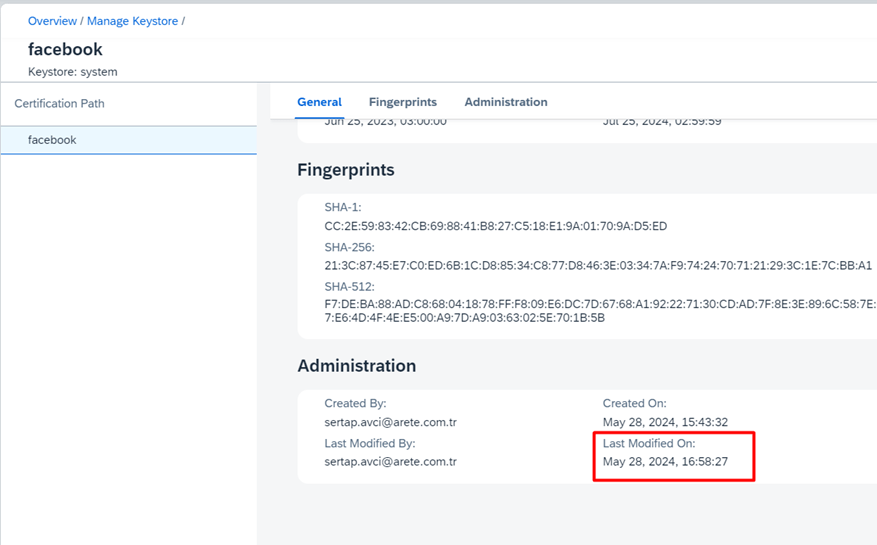
Certification dates before operation
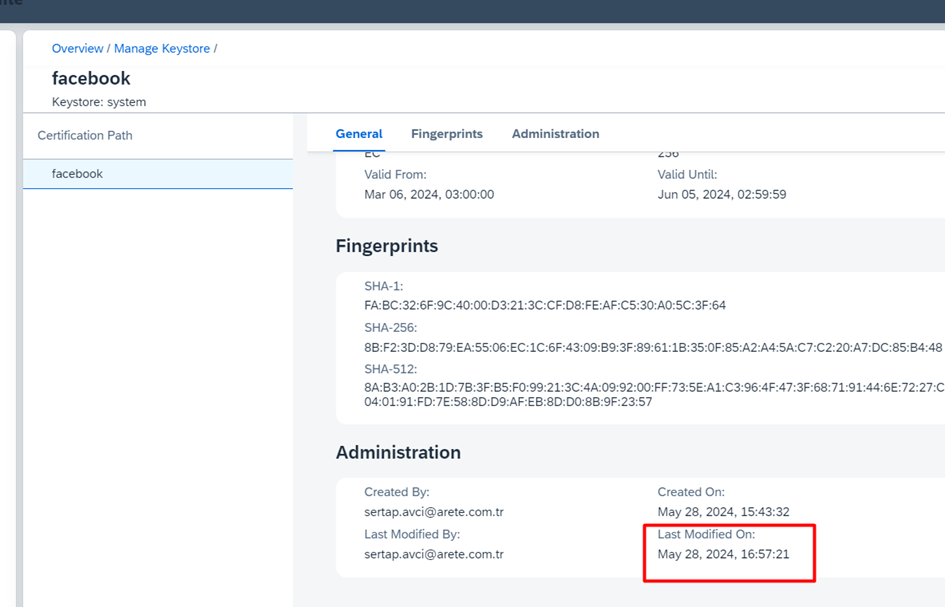
When we run the integration, it is updated as follows:
You can understand that the imported certificate has changed when the date below is updated.