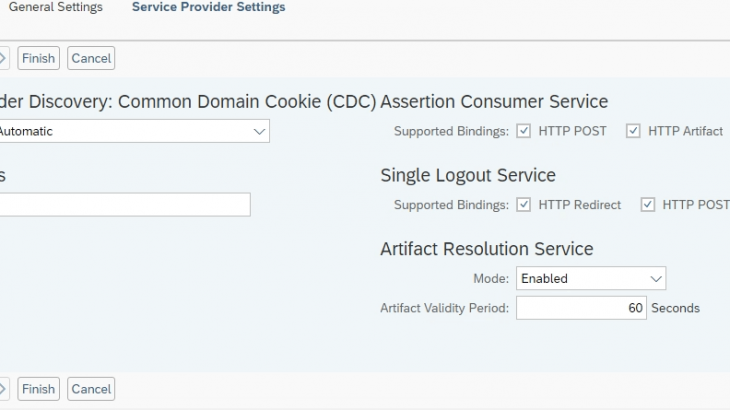
In this session, I am going to discuss about the SSO implementation for SAP analytics cloud with BW live connection with IdP (In our case it is Azure AD). In most of the implementation project when you develop SAC stories for business users, your mail goal is to make popular your dashboards and stories which […]